Table of contents
Who is Warlock ransomware group?
The Warlock ransomware group first emerged in early June 2025 on the Russian-language RAMP cybercrime forum advertising its services. A bold post proclaimed: “If you want a Lamborghini, please contact me.”
Commonly seen with other ransomware groups, Warlock operates using the ransomware‑as‑a‑service (RaaS) model, allowing other ransomware operators to use their ransomware and platform for a price. Operators, frequently called affiliates, use resources provided by the ransomware group, such as the ransomware builder, a playbook with relevant tools, the victim management platform, and a victim data leak site to conduct successful attacks and extort organizations. Warlock affiliates are responsible for each attack stage, starting with initial access and ending with ransomware deployment.
So far, technology, telecommunications, financial services, manufacturing, and agriculture are the primary target industries. The group claims the majority of its victim organizations reside in the United States, the United Kingdom, Japan, India, and France.
Warlock ransomware affiliates and operators
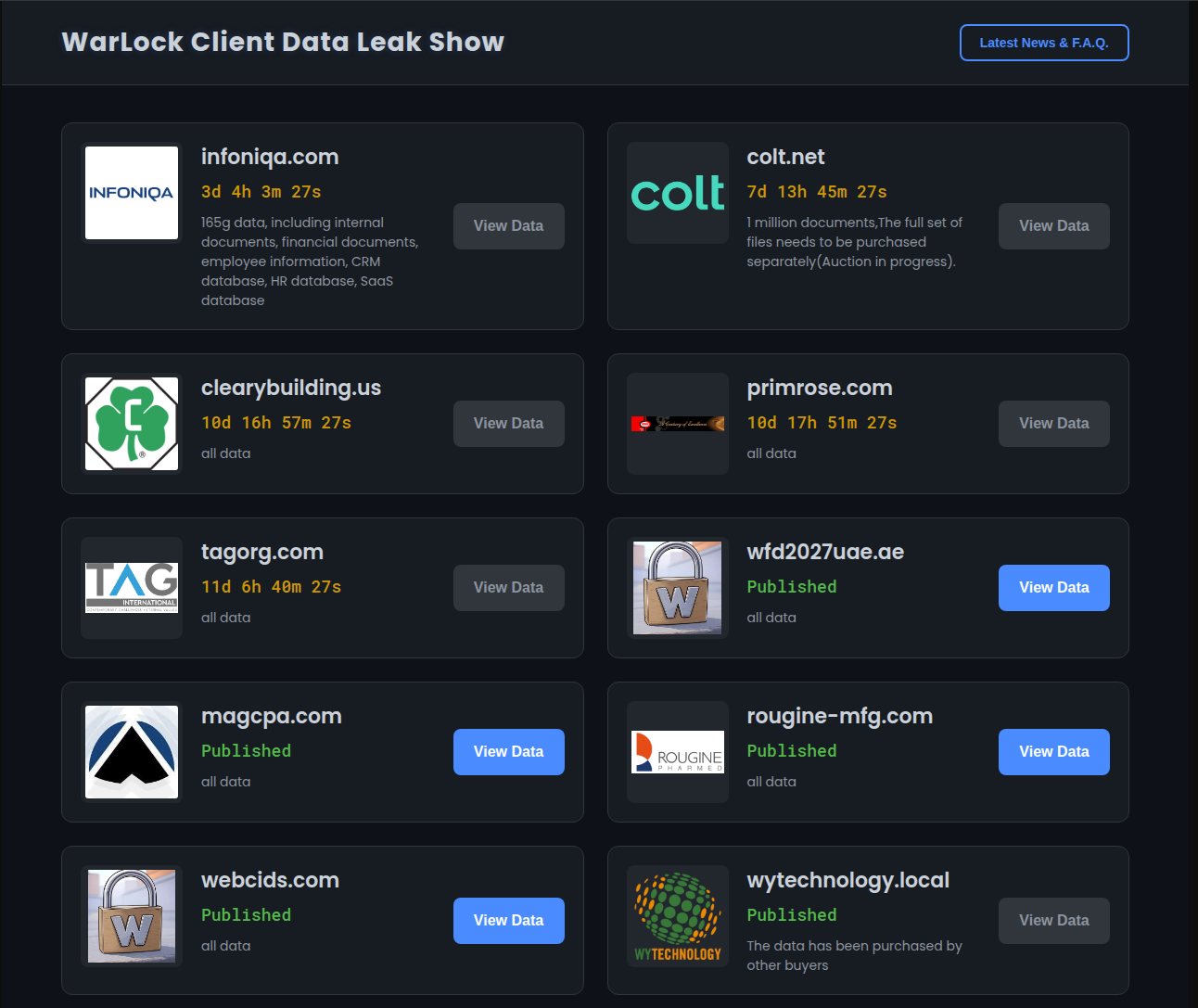
Cybercrime forum RAMP user "cnkjasdfgd" claimed responsibility for the Colt Telecom attack. Another known affiliate, Storm-2603, was identified by the Microsoft Threat Intelligence Team as a potential Chinese hacking group, known for leveraging the ToolShell vulnerability chain to deploy Warlock ransomware on victim hosts.
Warlock ransomware attack chain: From access to impact
Initial access
A threat actor using Warlock is believed to have gained initial access by exploiting unpatched on-premises SharePoint servers vulnerable to CVE-2025-49706 & CVE-2025-49704 (ToolShell).
Defense evasion
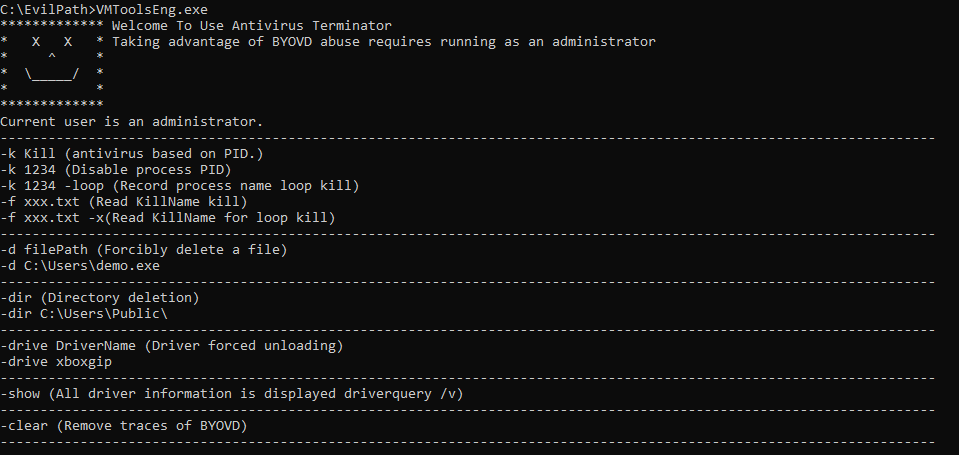
With initial access through the compromised SharePoint server, Storm-2603 has been observed deploying a vulnerable third-party driver and a custom executable designed to terminate antivirus solutions and protected processes. The executable named “Antivirus Terminator” is capable of terminating processes by PID, deleting files/folders, unloading other drivers, and removing evidence of execution. The vulnerable driver, identified as “AToolsKrnl64.sys” but named “ServiceMouse.sys”, is signed by “Antiy Labs” and is a component of their “System In-Depth Analysis Toolkit” product.
Persistence & command and control
To maintain access on the compromised SharePoint server, two additional executables are deployed: “AK47DNS” and “AK47HTTP”, both of which are part of the AK47 C2 framework. As their names suggest, the “AK47DNS” variant utilizes uses DNS for communication with the command and control server, and the “AK47HTTP” variant relies on HTTP. Both will attempt to evade detection from the user by hiding the attached console window on launch.
Lateral movement
The primary method of moving laterally throughout the environment from the SharePoint server is the Sysinternals PsExec utility, which allows threat actors to execute commands on other target hosts remotely, and subsequently obtain access. Additionally, remote management software and Windows Remote Desktop have also been observed as means for lateral movement, although less frequently.
Exfiltration
Once sufficient access is obtained, exfiltration of sensitive data starts. This depends on the victim organization’s industry, but the standard types of data that are extracted are company financial records, employee data, and client data.
Impact
After data exfiltration is complete, the final step involves deploying the Warlock ransomware executable and then exiting the network.
Warlock Ransomware Technical Analysis
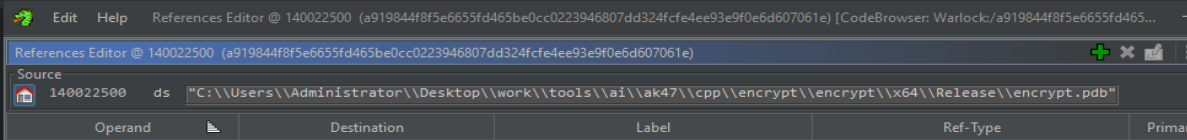
Older and newer samples of Warlock have undergone drastic changes since their initial debut, evolving from including PDB file paths with extra options to stripping the binary and removing certain functions; however, the overall functionality remains the same. The ransomware binaries that Warlock deploys are part of the AK47 project, which is referenced in the PDB path embedded in the ransomware executable.
When the ransomware file executes, it first checks for the presence of the following arguments “-e”, “-n”, and “-p”.
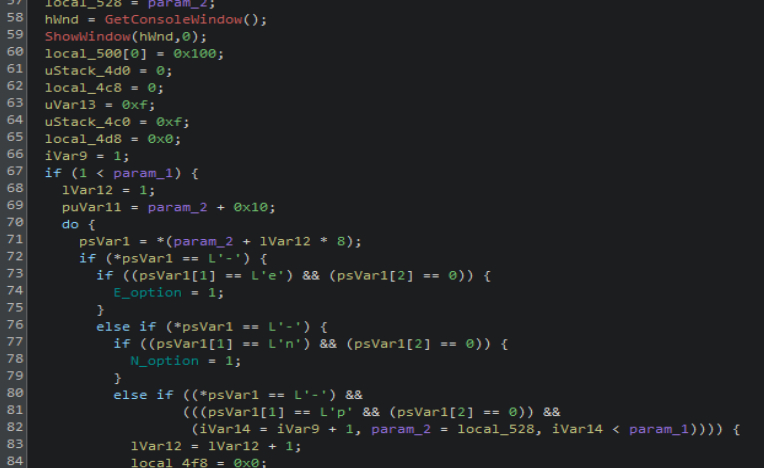
The newer variant includes a hostname kill switch designed to prevent users from accidentally executing the ransomware on their own development and operator computers. In this sample, it doesn't have a list of hosts to check for and instead has the placeholder value "replacethiswhitehost".
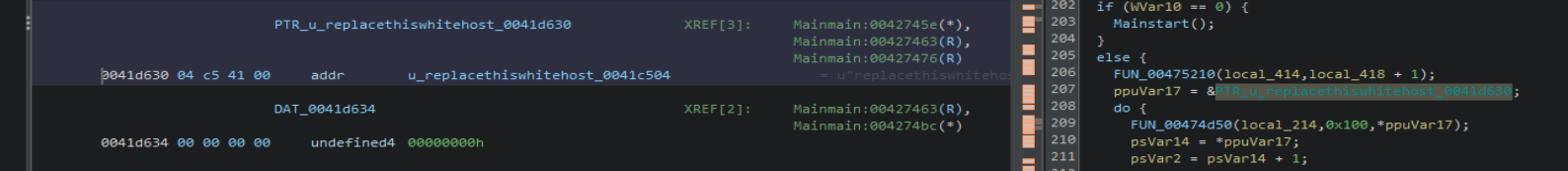
Both variants will check the last access date of the following Windows files. For this sample, if the last accessed date for any of the files matches or is later than “9/9/2026 00:00:00”, the ransomware process exits.
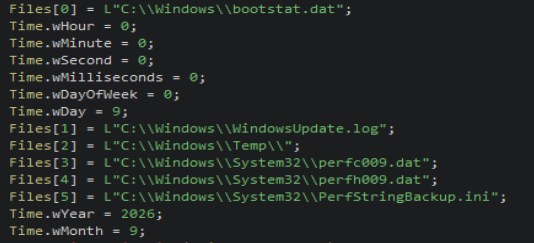
Once all the safety checks have completed, the ransomware will query the list of device drives and terminate the listed processes and services, including antivirus and backup software. Following process termination, volume shadow copy service snapshots are forcibly deleted using Component Object Model (COM), instead of the more common “vssadmin” and “wmic” equivalents. Shortly after, the main ransomware worker threads which are responsible for file encryption and dropping the ransom note are created.
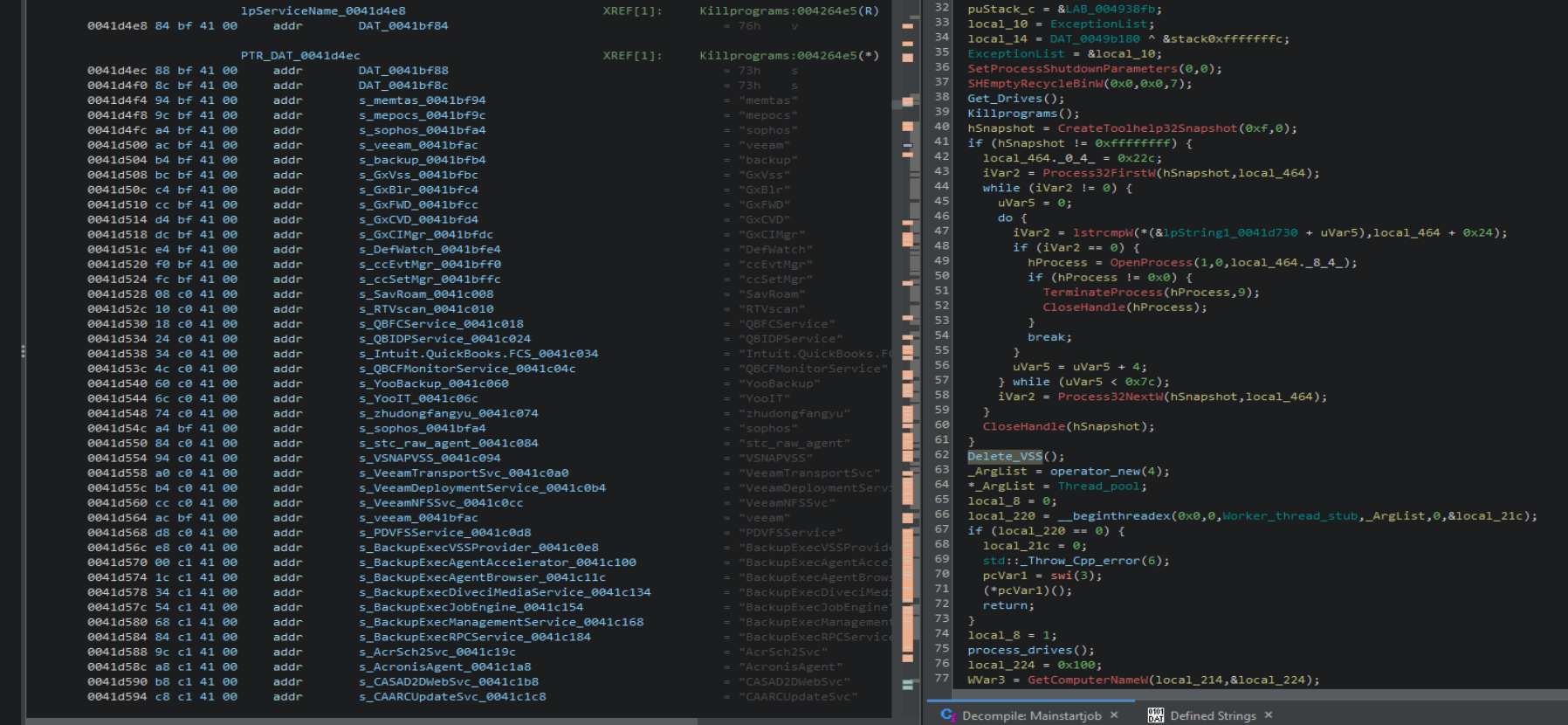
Each worker thread will traverse directories to identify target files, and queue them in batches for file encryption. Windows system files, dropped ransom notes, previously encrypted files, and files that match a hardcoded extension list are skipped.
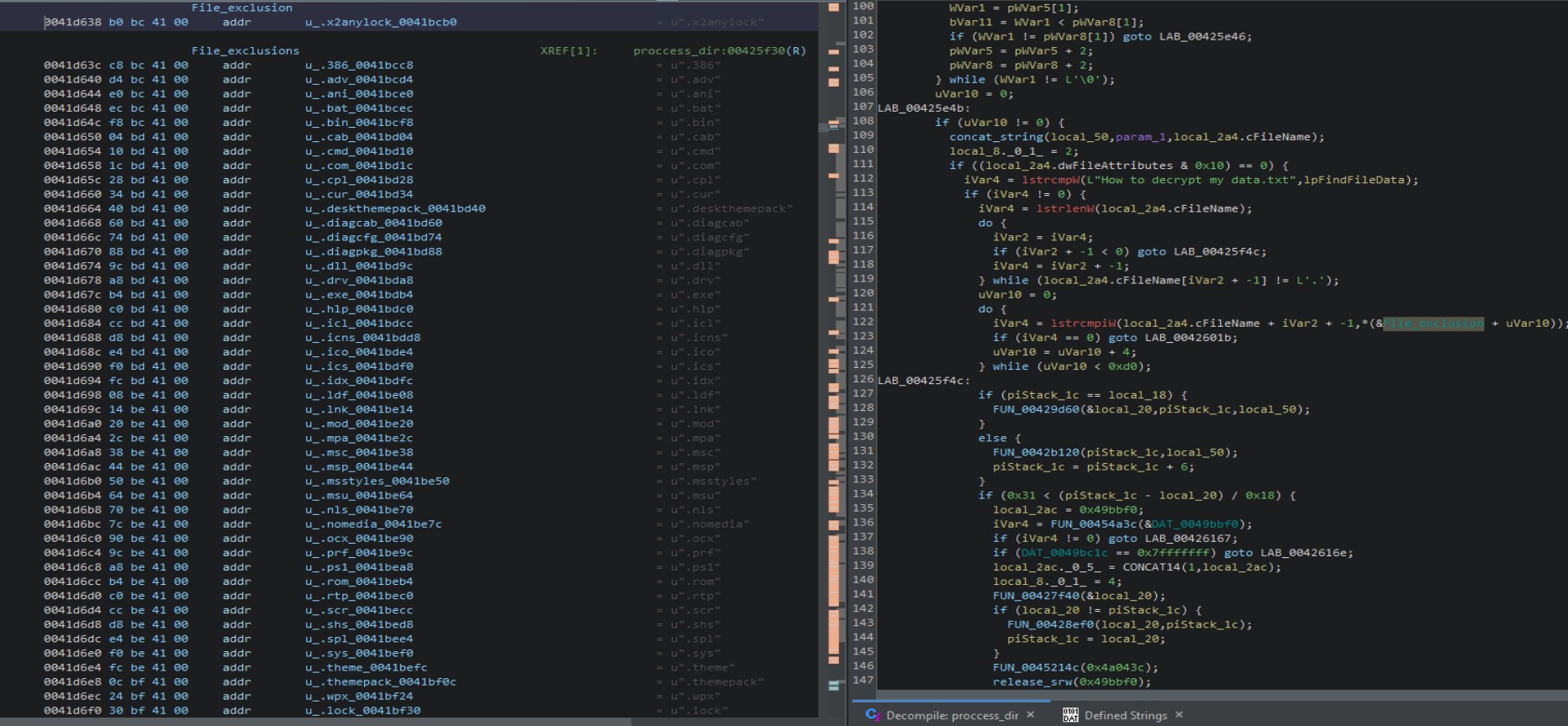
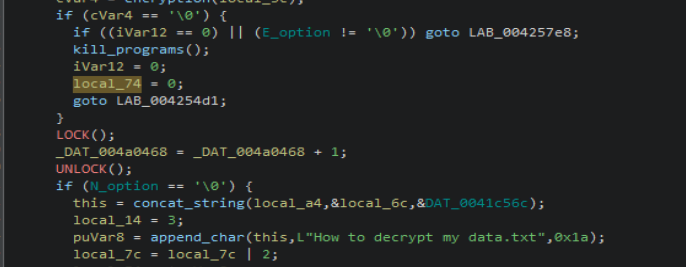
Prior to file encryption, the flags set by the “-e” and “-n” are checked. If “-e” is present, encrypted files will not be renamed instead of the default use of the .x2anylock extension. If “-n” is present, the ransom note will not be written to disk.
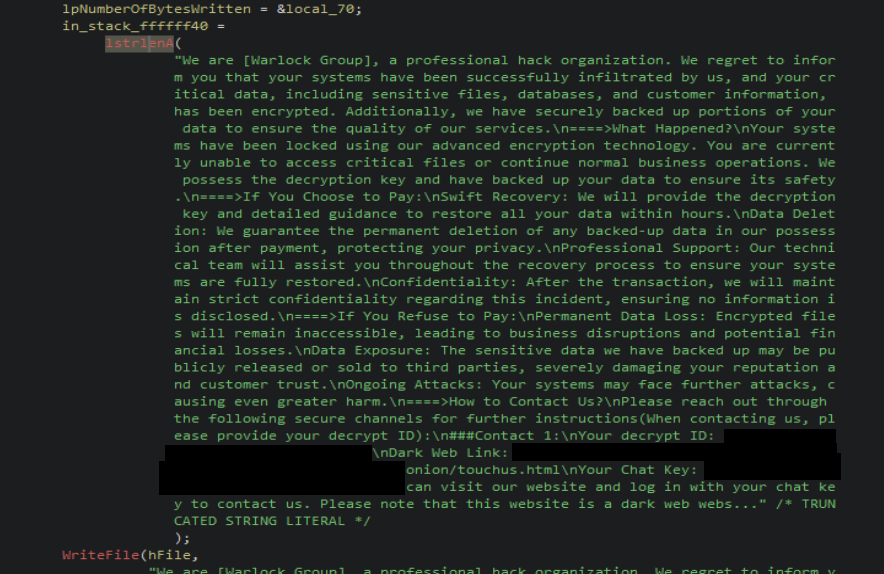
The ransom note content is hardcoded in both variants of the ransomware in plaintext, instead of reading it from an encrypted config section, commonly seen in other ransomware families.
Warlock ransomware IoCs (Indicators of Compromise)
- .x2anylock
- How to decrypt my data.log
- How_to_decrypt_my_data.txt
- a919844f8f5e6655fd465be0cc0223946807dd324fcfe4ee93e9f0e6d607061e
- f711b14efb7792033b7ac954ebcfaec8141eb0abafef9c17e769ff96e8fecdf3
- aca888bbb300f75d69dd56bc22f87d0ed4e0f6b8ed5421ef26fc3523980b64ad
- d1f9ace720d863fd174753e89b9e889d2e2f71a287fde66158bb2b5752307474
How ThreatLocker can help
Application Allowlisting and Ringfencing™
ThreatLocker Application Allowlisting can block applications that are not explicitly permitted by ThreatLocker, such as unauthorized Remote Monitoring and Management (RMM) applications.
Additional explicit deny policies can be created to prevent the usage of high-risk applications, such as Python, MSBuild, vssadmin, and PsExec.
For applications that are high-risk, but are required by business processes, policies with Ringfencing can be used to restrict what resources applications can interact with, such as specific files, internet access, the registry, or executing other applications.
Storage Control
ThreatLocker Storage Control monitors and can prevent access to files and file folders according to your rules. Files created or enumerated by Warlock ransomware would immediately generate events in the Unified Audit or be blocked entirely.
Network Control
ThreatLocker can limit ransomware operators from accessing your organization network by utilizing Network Control to block non-ThreatLocker monitored devices from accessing resources such as Remote Desktop, Windows Remote Management shell, and PsExec from the edge VPN or firewall.
ThreatLocker Detect and MDR
ThreatLocker Detect can identify behavior such as ransomware deployment, security service tampering, backup deletion, or data exfiltration, and alert your organization's internal security team or the Cyber Hero Managed Detection and Response team.
Learn more
To learn more about ThreatLocker solutions, book a demo customized to your environment and needs.







