Network Control
Network Control is an endpoint firewall solution that gives control over all network traffic, so you don’t leave devices or data vulnerable and exposed to cyber threats.


What is Network Control (Network Access Control)?
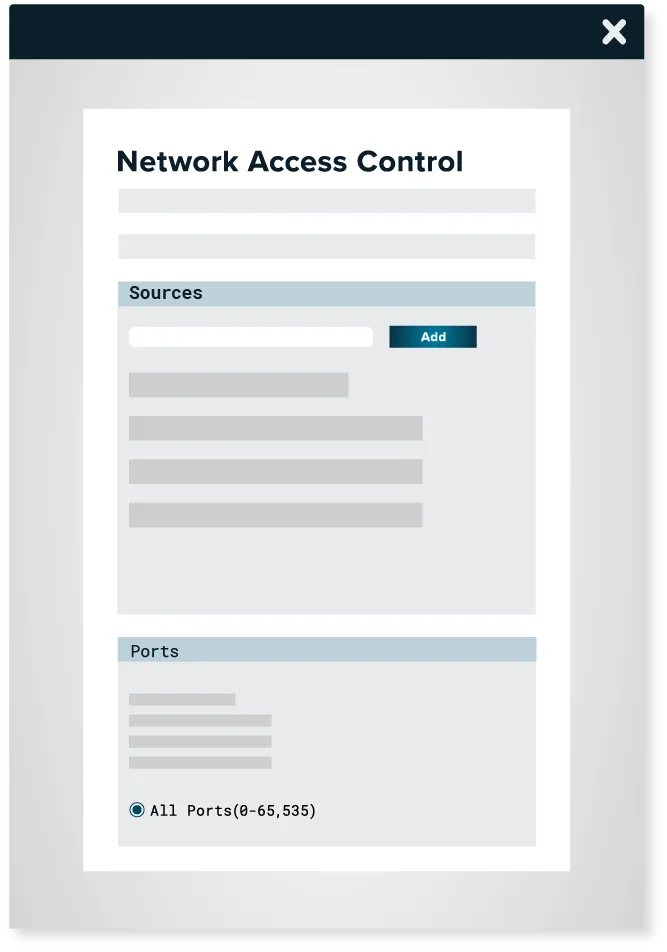
ThreatLocker® Network Control is a firewall for endpoints and servers that can be managed centrally. It provides complete control over network traffic, which helps to protect your devices. Custom-built policies are used to grant access to the network based on IP address, specific keywords, agent authentication, or dynamic ACLs. This network access security tool allows granular control over access to the network.

Why Network Control?
The local network is no more. Neither is the corporate firewall. Users are not only working from the office but also remotely, meaning the network we utilize has quickly become the internet, leaving devices and data vulnerable to cyber threats. This dissolution of the business perimeter makes network access controls essential to protect your devices and, by extension, your data.
The ThreatLocker network access control solution helps protect business assets whether employees are in the office or remote. ThreatLocker Network Control provides a direct connection between the client and server, as opposed to a VPN that goes through a central point.
ThreatLocker whitepaper: Network Control
Discover how ThreatLocker® Network Control fortifies your network security while seamlessly integrating with the full ThreatLocker® Zero Trust Endpoint Protection Platform.
How does Network Control work?
ThreatLocker network security tools help you manage firewall policies and port control for all devices from one place. Traditional firewalls rely on static ACLs to control access to network assets, requiring IT intervention to make changes. Employees who travel or change locations frequently need the IT department to adjust the firewall for each new location.
ThreatLocker uses dynamic ACLs to adjust the firewall without user interaction. Create custom policies to open ports on demand for approved devices and users, no matter where they connect from.
Once an authorized device no longer uses the open port, it will automatically close within 5 minutes. Unapproved devices will not be able to connect to or have visibility of the open port.
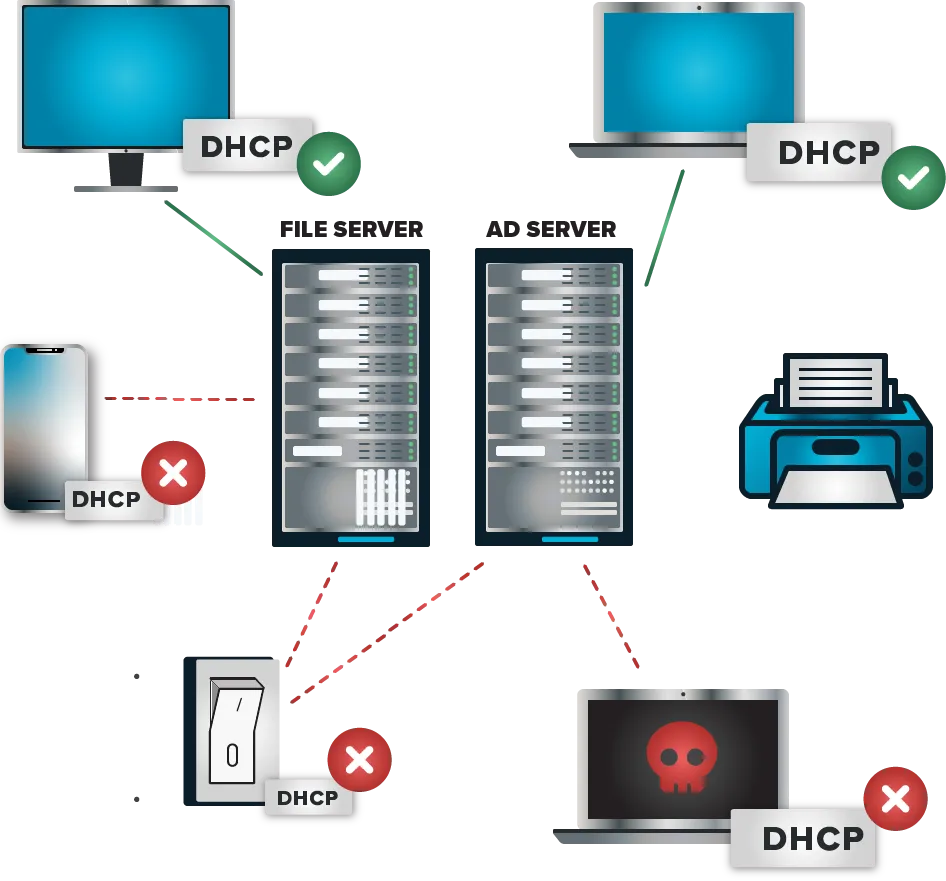
The ThreatLocker® difference
Traditional NAC security solutions focus on broader network access control. ThreatLocker Network Control focuses on controlling and securing individual endpoints.
The ability for such granular control empowers enterprises to allow or deny specific applications or processes from running, communicating over the network, or accessing particular resources. Network security monitoring tools make enforcing your security policies easier and protect your data no matter where your employees work.
NETWORK CONTROL FEATURES

Configurable
Using global and granular policies, NAC security allows users to configure network access to endpoints.

Cloud-based
The cloud-managed solution provides customers with a centralized view of endpoint policies and network traffic across your organization.

Dynamic
NAC enables users to deny all traffic to published servers while only allowing a single computer by IP address or dynamically using a keyword. This is great for a user who is often traveling.

Enhanced security
Ensure rogue devices on your network cannot access your servers or endpoints with Dynamic ACLs.
More ThreatLocker® solutions





