Application Allowlisting
Allow only the software you need, and block everything else - including ransomware.


What is Application Whitelisting (Allowlisting)?
Application Allowlisting, previously known as "Application Whitelisting," works by a simple rule: if it's not expressly permitted, it's blocked. This robust form of access control prevents untrusted software, including all types of malware and ransomware, from running. It's a key part of endpoint security that ensures only specific, safe applications operate on your network.
Why Allowlisting?
Considered a top-tier security strategy, Application Allowlisting gives you control over which software, scripts, and libraries run on your devices and servers. It's more effective than traditional antivirus or EDR solutions. Application Whitelisting blocks not just malicious software but also any unauthorized applications. This greatly reduces the chances of cyber threats and rogue programs affecting your network, protecting your sensitive data.
watch the webinar
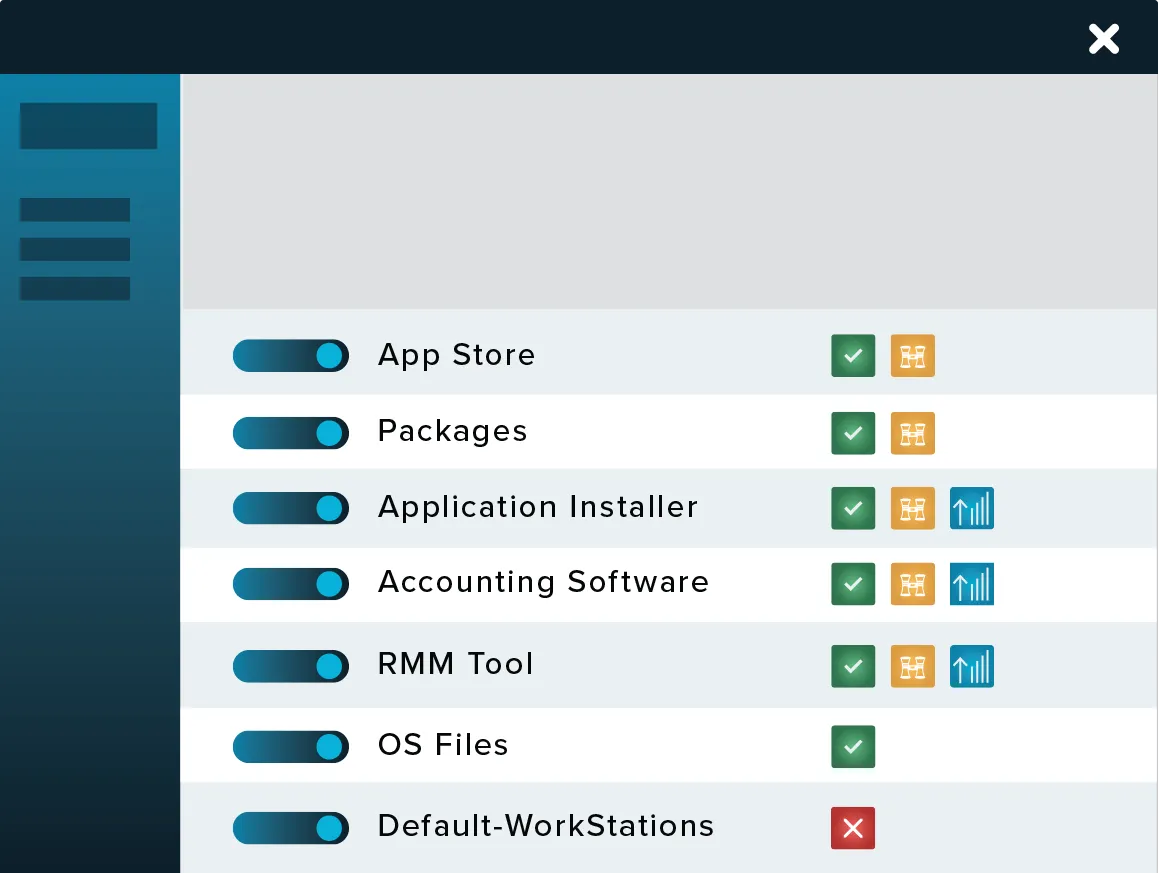
How does Application Whitelisting (Allowlisting) work?
Approval process
Going forward, employees can no longer download any application they choose.
Here’s the good news: they can request access for blocked apps via a popup, which your internal IT or the ThreatLocker Cyber Hero team can approve within minutes.
This approach provides full visibility and control over what runs, when, where, and by whom, eliminating shadow IT and unauthorized software.
Learning Mode
When your organization first gets started with ThreatLocker Application Allowlisting, it deploys Learning Mode, which automatically catalogs applications in your firm’s network.
After a few days or few weeks–depending on the size and complexity of your environment–ThreatLocker has a complete inventory of the apps running on every endpoint.
Then comes the transition. ThreatLocker green lights a tailored list of apps, ensuring only trusted software runs. The rest are automatically denied.
The buyer's checklist for Allowlisting
We've compiled this free checklist to make it easy to understand the non-negotiable features that any Allowlisting solution should have.
Eliminate the risk and guesswork of Application Whitelisting
In addition to Allowlisting, ThreatLocker Testing Environment is a powerful tool that allows for risk-assessed approvals that eliminate the guesswork.
The Testing Environment enables administrators to evaluate new applications thoroughly within a virtual desktop infrastructure (VDI). This real-time analysis provides the necessary insight to make informed decisions, enhancing your overall security solutions against malware attacks.
ALLOWLISTING FEATURES

Deny by default
Deny any application from running on your device that is not a part of the allowlist.

Firewall-like policies
A powerful firewall-like policy engine that allows you to permit, deny or restrict application access at a granular level.

Time-based policies
Permit access to applications for a specified amount of time. Automatically block the application after the policy has expired.

Automatic updates
ThreatLocker automatically adds new hashes when application and system updates are released, allowing your applications to update without interference while preventing updates from being blocked.
FREQUENTLY ASKED QUESTIONS
The goal of Zero Trust is to only allow what is needed and to block everything else. To stop business interruption, ThreatLocker will automatically learn what your environment requires, and will build policies that include applications and their dependencies in Learning Mode. The first step is to deploy the agent, which can be deployed using various automation tools.
The agent will not block anything during the initial deployment; instead, it will go into Learning Mode. After a week of learning, you can review the list of policies that have been created, then deny or limit any software you do not want and secure your environment.
Yes, in the sense that ThreatLocker adds the newest version of the application to the built-in definition for use in a policy; however, ThreatLocker does not currently support approving specific versions of a built-in application
Yes, ThreatLocker allows you to create multiple policies for an application to further restrict access by User or by Group.
Most companies are secured in under a week. Almost all are 10 days or under.
Before you secure your environment, you will have the option to simulate potential denies based on a period of time. This will ensure no strange applications will cause issues.
ThreatLocker will walk you through this process by scheduling weekly calls to deploy, review policies, and help you secure your environment.
A typical deployment in a medium to large business should take about 5 calls from deployment to fully secured.
Ultimately, your IT administrator decides what should be allowed to run. The ThreatLocker learning process will create a list of policies, which you can review and amend before enabling protection and securing your systems.
ThreatLocker does not allow applications simply because they're from an approved vendor. From a cybersecurity perspective, the fewer applications are permitted to run in an environment, the better. Allowing all applications by a specific vendor or vendors flies in the face of this approach.
ThreatLocker runs at the kernel level, meaning it doesn't matter if something is executed by an administrator, system, or user, if it hasn't been allowed to run via the Allowlist, it will be blocked.
ThreatLocker also has extremely stringent tamper protection, which, combined with its kernel level services, makes it nearly impossible to interfere with its operation.
Allowlisting may block changes to the application if the application updates. ThreatLocker solves this problem by having a predefined list of built-in application definitions. If you have a policy for a built-in application, ThreatLocker will automatically update the policy when new updates are released. Our team monitors over 10,000 tracked applications, and updates the definitions 24/7/365.
For unknown applications that have automatic updates, your Solutions Engineer can help you create custom rules and definitions using a combination of hashes, filenames, calling processes, certificates and creating processes. If the IT team deploys the update, you can use installation mode to track the changes by the installer.
The ratings coming from our internal system based on the business use case of the application as well as both previous and current exploits of vulnerabilities in that application.
At the moment, we cannot make an exception to a Global policy with a policy at another level. You can still use Users/Groups to make exceptions at the Global level.
Yes. Application Control controls any executable's ability to run on your endpoints.
Absolutely. We provide multiple secure ways to allow new applications. You can utilize our built-ins or use installation mode in our virtual testing environment.
ThreatLocker support is available 24/7/365 and is accessed via a chat function on the portal. All chats are answered within 60 seconds, and our Cyber Hero team can assist via chat or Zoom. We also have an extremely comprehensive knowledge base, as well as ThreatLocker University, which provides self-paced a la carte courses, or pre-determined learning tracks up to Cyber Hero Certification.
start Your path to stronger defenses
Get a trial
Try ThreatLocker free for 30 days and experience full Zero Trust protection in your own environment.
Book a demo
Schedule a customized demo and explore how ThreatLocker aligns with your security goals.
Ask an expert
Just starting to explore our platform? Find out what ThreatLocker is, how it works, and how it’s different.