Table of contents
Introduction
When a vendor’s security systems fail, the consequences can extend far beyond their boundaries. The 2024–2025 Cierant Corporation data breach demonstrated how quickly one vendor’s compromise can evolve into lawsuits, reputational fallout, and long-term financial cost for every organization connected to it.
Cierant Corporation, a Connecticut-based marketing firm serving the health care industry, is now the subject of a consolidated federal class action. The case illustrates the widening liability that comes from third-party software, vendor integrations, and complex data chains that blur where responsibility begins and ends.
What happened
According to Cierant Corporation’s July 2025 incident notice, the company detected suspicious activity in its environment on December 10, 2024. Investigators found that attackers had exploited a vulnerability in Cleo VLTrader, a third-party file-transfer tool. The notice explains that Cierant engaged a cybersecurity firm to investigate and later confirmed that an unauthorized actor accessed files of members of U.S. health plans whose communications were processed by Cierant, those files containing names, addresses, dates of birth, treatment-related dates, provider names, medical record numbers, health plan beneficiary numbers, claims numbers, and plan member account numbers.
Cierant reported the breach to the U.S. Department of Health and Human Services Office for Civil Rights, identifying 232,506 affected individuals. Further, Cierant has said that no Social Security or financial account numbers were involved.
Plaintiffs claim the company’s safeguards were inadequate and that the delay between discovery and notification violated consumer-protection statutes. They also allege that Cierant’s failure to apply available patches for Cleo VLTrader promptly contributed to the incident.
The people involved
The breach gave rise to several individual class actions during the summer of 2025, including Shields v. Cierant Corporation, Credle v. Cierant Corporation, Verriere v. Cierant Corporation and Blue Cross Blue Shield of Massachusetts, Gifford v. Cierant Corporation, and Almaz v. Cierant Corporation. Each complaint alleged negligence, failure to implement reasonable data security, and untimely notification.
The plaintiffs each have their own story about how the breach changed their lives.
California resident Anthony Almaz said he had to invest a lot of time monitoring accounts and saw a noticeable increase in spam calls and texts.
Melissa Gifford of New Jersey said she became worried about her child, whose data was caught in the breach. She said she has feared identity theft, medical identity theft, and fraud, including misuse of minors’ identities.
Rashon McMiller, a Texas resident, claimed anguish, stress, and annoyance, out-of-pocket expenses for credit monitoring and identity-theft protection, and productivity lost to “taking time to address and attempt to ameliorate, mitigate, and deal with the consequences of” the breach.
Meanwhile, Cierant is based in Danbury, and according to several online directories, employs less than 50 people. The specialized omnichannel marketing vendor bills itself as a “health insurance communications innovation company” that provides a technology platform for health plans: “tailoring your marketing and member communications to an audience of one … integrate[s] with print-on-demand, online channels … multi-touch campaigns.”
Health organizations like Blue Cross Blue Shield of Massachusetts, which is one of the health insurers named in the case, have looked to Cierant for marketing support since 1987.
Multiple lawsuits consolidated to one case
In September 2025, Judge Kari A. Dooley of the U.S. District Court for the District of Connecticut consolidated these cases into one. This procedural step transforms what began as scattered consumer actions into a central test case for vendor accountability in data-processing relationships.
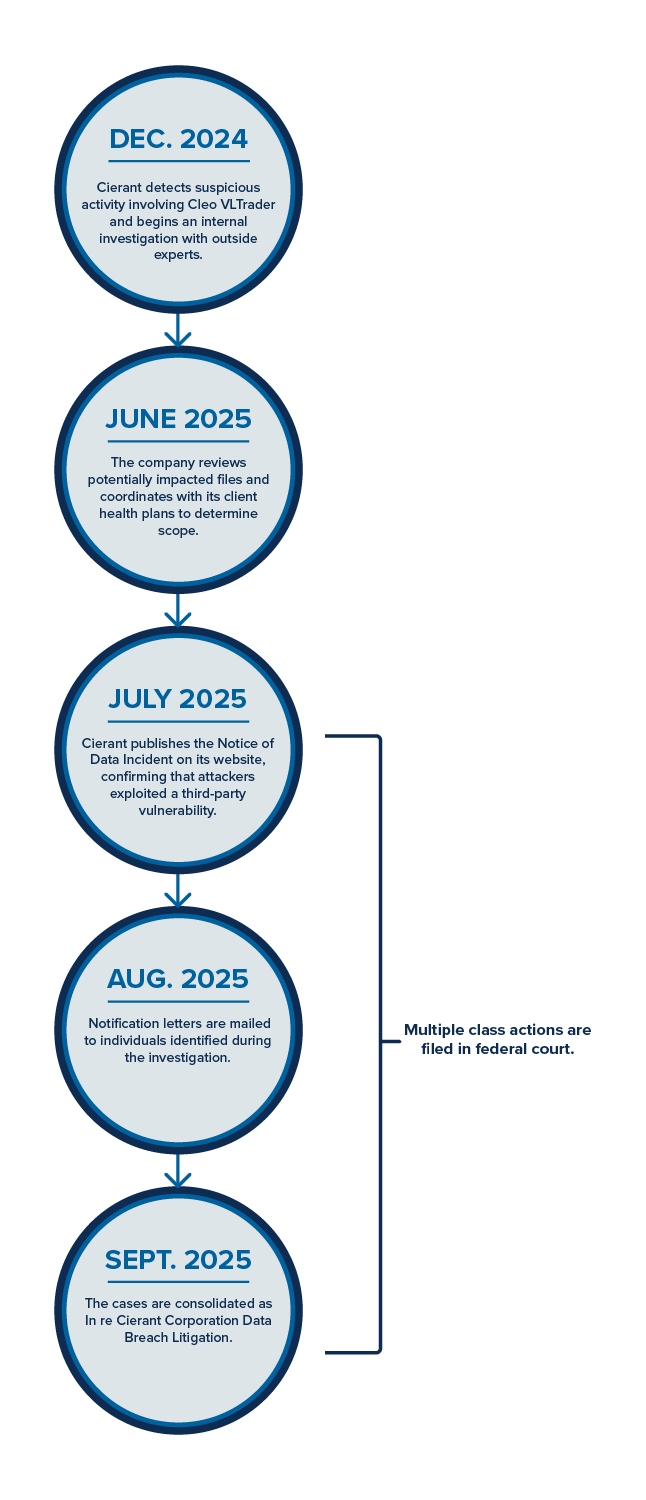
The timeline of the Cierant data breach escalation
Based on Cierant’s own Notice of Data Incident and federal filings, the following timeline is documented:
The plaintiffs argue that the seven-month gap between discovery and public disclosure violated breach-notification laws in numerous states. Cierant’s timeline, which it disclosed voluntarily, establishes the sequence but not the legality of the delay. The adequacy of its response is now a question before the court.
The legal exposure
The consolidated complaint seeks compensatory damages, statutory damages, and injunctive relief. The plaintiffs have asked the court to require independent audits, multi-year security assessments, and lifetime credit monitoring for those affected. The filings cite Cierant’s contractual duties to safeguard protected health information under federal and state law.
Even without a costly verdict, such litigation imposes substantial cost through defense, remediation, and loss of client confidence. For CISOs, the case underscores how vendor oversight has evolved from a procurement issue into a security governance responsibility at the board level.
The Cierant breach reveals the fragility of modern supply chains. The defendant was not the originator of the vulnerability; Cleo VLTrader allegedly was. Yet clients and regulators still hold Cierant accountable. The lesson is that security obligations cannot be delegated. The law sided with plaintiffs in similar cases including well-known Target, Experian, Equifax, Neiman Marcus, and Hannaford breaches.
The filings highlight several risk areas that CISOs must confront directly:
- Third-party dependency: A single vendor’s software can extend a vulnerability across hundreds of customers.
- Notification delays: Every day between discovery and disclosure increases legal and reputational exposure.
- Regulated data handling: Industries like health care and insurance data carry higher obligations for encryption, segmentation, and retention control.
For leaders managing vendor ecosystems, these points define the next phase of accountability.
Governance lessons from the Cierant case
Vendor software is part of your perimeter
Treat vendor applications as extensions of your own environment. Perform initial third-party security assessments whenever possible using a questionnaire specific to each new vendor relationship. After integrating with them, continuous monitoring of patch cycles, secure configurations, and data flows is essential.
Notification speed defines credibility
A well-written breach plan means little without rehearsed timelines. Regular tabletop exercises should include scenarios where a vendor breach triggers your notification duties. In each business agreement with a new vendor, security breach notification timelines and other service SLAs should be clearly defined.
Data minimization limits impact
Vendors should list each category of data they collect and why. Require them to justify the categories of data they store and to demonstrate encryption at rest and in transit. If the amount of different data types they collect seems overboard, ask them to modify their agreement. The more data they collect, the more you are liable to protect.
Document your oversight
Courts and regulators evaluate evidence, not intention. Keep records of vendor risk reviews, contract language, and audit results.
Align legal and security teams
The Cierant litigation shows that delays often occur when legal review and technical response operate separately. Joint readiness reduces action hesitation.
Vendor-risk readiness checklist for CISOs
IT Operations
- Take a routine inventory of all vendors and software integrations.
- Require vendors to provide patch report documentation and proof of vulnerability management.
- Restrict vendor access to local assets to accounts secured with multifactor authentication.
GRC and Compliance
- Maintain a central register of vendor risk ratings.
- Map each vendor's security posture, measured by their questionnaire answers, to compliance requirements such as HIPAA, GLBA, or GDPR.
- Specify notification timelines and breach-response duties in every contract.
Security Architecture
- Segment vendor applications to a separate network, DMZ, or VLAN.
- Restrict network connections from vendor processes to verified domains only.
- Monitor for anomalous activity from trusted applications.
CISO and Executive Oversight
- Include vendor breach scenarios in incident-response testing.
- Track compliance metrics on your own network and software, such as average patch latency and severity of missing patches.
- Apply classification labels to your data and require SOC 2 Type 2 or equivalent certification for vendors hosting anything sensitive.
How ThreatLocker protects against vendor-origin breaches
Application Allowlisting and Ringfencing™
Only approved executables can run, which blocks unauthorized vendor tools, malicious updates, and any software that hasn’t been explicitly allowed by your security team. Adding Ringfencing™ will confine what approved applications can access, preventing data movement outside intended boundaries.
Storage Control
Granular access policies stop compromised vendor software from reading or exporting sensitive files, locally and across network shares.
Network Control
Endpoint firewall rules dynamically block network traffic to unknown destinations. Traffic sessions to trusted vendor addresses automatically close after five minutes of inactivity.
ThreatLocker Detect and MDR
Behavioral monitoring identifies abnormal vendor-application activity, unauthorized encryption, or large-scale data transfers. Detect can isolate affected systems within minutes while the MDR team provides continuous human oversight and alert response.
These layers turn Zero Trust from a framework into a measurable defense against supply-chain breaches like the one at Cierant.
FAQ
- What caused the Cierant data breach?
Attackers exploited a vulnerability in Cleo VLTrader, a third-party file transfer tool used by Cierant, which allowed unauthorized access to healthcare-related data.
- How many people were affected by the breach?
According to Cierant’s report to the U.S. Department of Health and Human Services, 232,506 individuals were affected.
- Why is the Cierant case important for CISOs?
The case shows that organizations are legally and reputationally accountable for vendor security, even when the initial vulnerability originates from a supplier.
- What legal action has been taken against Cierant Corporation?
Multiple class actions have been consolidated into In re Cierant Corporation Data Breach Litigation in the U.S. District Court for Connecticut.
- How can companies reduce the risk of vendor-origin breaches?
Enforce least privilege, segment vendor apps, define breach notification timelines, and use Zero Trust tools like ThreatLocker to contain vendor-origin threats.