Table of contents
Inside the Penn breach
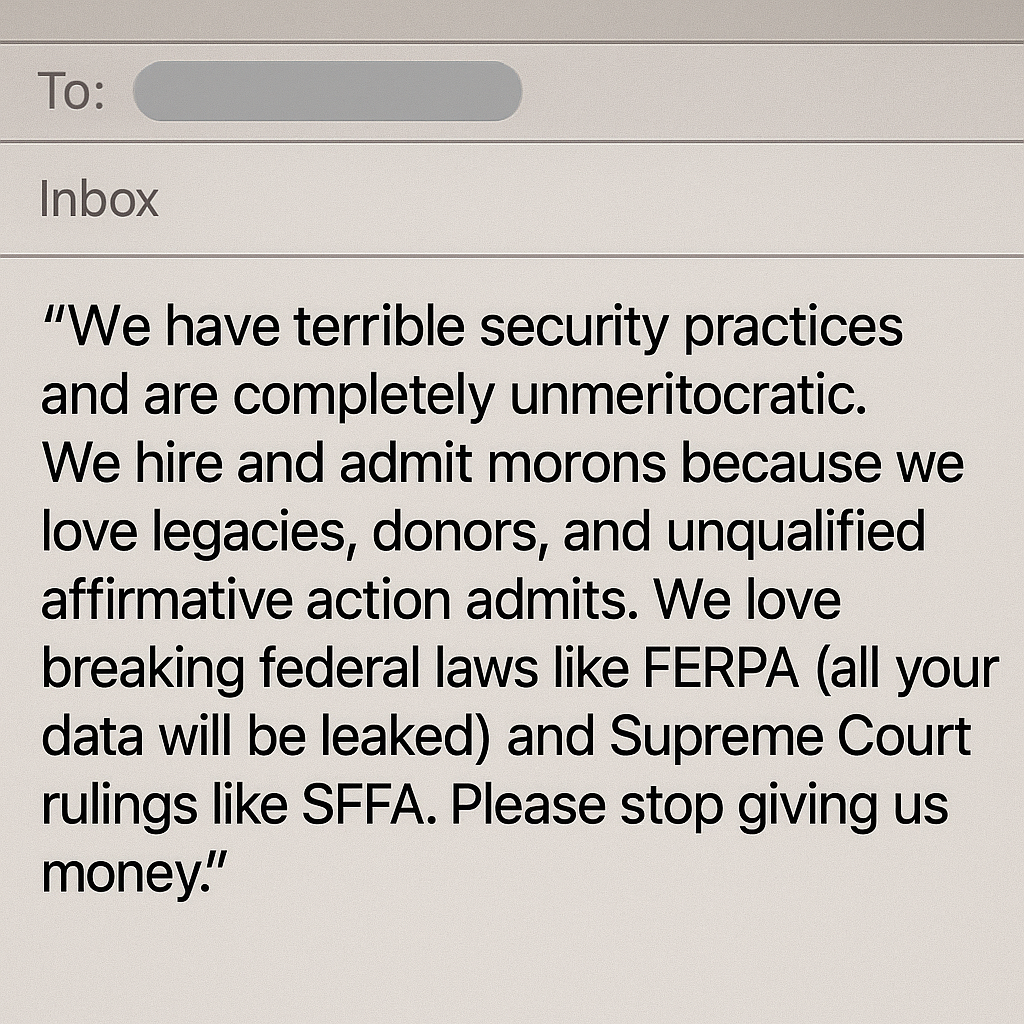
This wasn’t a prank email. It was a snarky declaration sent to hundreds of thousands of students, faculty, alumni, parents, and even some people outside the university by attackers who hijacked accounts linked to Penn’s Graduate School of Education after compromising a PennKey login. It was meant to announce the breach and pressure the school by mocking its policies, threatening to leak data, and discouraging donations.
It was late October 2025 when inboxes began receiving the message from “@upenn.edu” addresses, mocking the university’s governance. Within days, screenshots of donor records, bank receipts, and internal communications appeared online.
Penn has joined the growing list of educational institutions learning the hard way that cyber risk is no longer theoretical—it’s reputational, financial, and existential.
From breach to courtroom
Within a week of the breach, plaintiffs from across the country had filed proposed class actions in federal court. Each alleges negligence and breach of duty for the exposure of donor and student data. The filings are still in the early stages, but they mark the beginning of a long legal process that will likely define how courts measure due diligence in higher-education cybersecurity.
The first complaints began arriving on November 4, only days after the breach went public. Mackey v. University of Pennsylvania was filed that day, followed by a wave of additional class actions through November 10. These include Lundy v. University of Pennsylvania, Smart v. University of Pennsylvania, Gade v. The Trustees of the University of Pennsylvania, Kim v. University of Pennsylvania, Sarmiento v. The University of Pennsylvania, and Rosenbaum v. University of Pennsylvania. Each seeks relief under the Class Action Fairness Act (CAFA), alleging Penn failed to secure personally identifiable information of students, alumni, donors, and staff.
Across the complaints, plaintiffs describe roughly 1.2 million records exfiltrated after attackers gained access via a compromised PennKey login, moving laterally into systems such as Salesforce, SAP, Qlik, and SharePoint. The suits claim negligence, breach of contract, breach of fiduciary duty, and unjust enrichment. Plaintiffs cite harm from identity-theft risk, emotional distress, and diminished value of their personal data. Each filing notes that Penn had acknowledged the breach and reported it to the FBI but had not yet detailed the technical root cause or offered credit-monitoring services.
The cost of the breach
Higher education institutions have become prime targets for financially motivated attackers, hacktivists, and state-backed groups alike. They hold research data, student identities, donor networks, and access to sensitive systems. Unlike private enterprises, universities often run on sprawling, federated IT structures that make consistent hardening difficult.
What happened at Penn followed a familiar pattern: A single compromised account, rapid lateral movement, and an information dump designed to maximize embarrassment. The breach disrupted communications, drew federal attention, and exposed systemic weaknesses in academic IT governance.
How higher education became a high-value cyber target
Stanford University ransomware incident (2024)
Stanford reported that its Department of Public Safety was hit by ransomware discovered on September 27, 2023. The university said attackers had been in the SUDPS network since May 12, 2023, and it began notifying about 27,000 affected individuals in March 2024. Data taken included personal information from department systems, and files were later posted by the threat group. The attack vector? A ransomware intrusion affecting the SUDPS network.
University of Michigan data exposure (2023)
On August 27, 2023, U-M severed campus internet and took systems offline in response to a significant security incident at the start of fall term. In October 2023, the university confirmed unauthorized access between August 23 and 27 and said personal data for up to 230,000 students, faculty, staff, and others was accessed. State officials reissued consumer alerts, and credit monitoring was offered. Attack vector: Not publicly confirmed. Context from U-M security alerts that year highlighted active phishing and attempts to bypass Duo two-factor authentication.
Lincoln College closure following ransomware (2022)
Lincoln College announced it would close permanently after 157 years, citing pandemic-driven financial stress compounded by a December 2021 ransomware attack that locked critical systems used for admissions, enrollment, and fundraising. The attack disrupted recruitment and retention operations during an already fragile period. Attack vector: ransomware; reporting links the event to compromised administrative systems, with initial access not conclusively detailed publicly.
The Blackbaud breach and third-party risk (2020)
Blackbaud, a major fundraising and alumni-relations vendor for universities and nonprofits, suffered a 2020 ransomware attack that led to data exfiltration. The company later acknowledged paying a ransom and in 2023, agreed to a $49.5 million multistate settlement over its security and breach response. Exposed data across thousands of clients included donor and patient information such as Social Security numbers, financial details, and health information in some cases. Attack vector: third-party provider compromise with data theft preceding ransomware.
The University of Greenwich legacy-site incident (2017)
The UK Information Commissioner fined the University of Greenwich £120,000 after attackers exploited an old conference microsite that was built in 2004 and left online, which exposed personal data for nearly 20,000 students and staff. Data included contact details and in some instances, sensitive information such as health-related notes, according to reporting on the ICO action and the university’s own statement. Attack vector: unretired legacy web infrastructure.
Across these examples, one pattern repeats: Some universities have underestimated the value of their data and perhaps also overestimated their immunity to commercial-grade threats. Whether it’s ransomware, credential theft, or plain misconfiguration, the cost is measured in court awards, downtime, and lost trust.
Lessons for academic cybersecurity leaders
Agnostic cybersecurity hardening checklist
1. Identity and access management controls
- Enforce multi-factor authentication (MFA) for all administrative and remote accounts.
- Apply least-privilege principles; remove legacy and shared credentials.
- Review directory permissions quarterly for both local and federated identities.
- Segregate high-sensitivity systems (research, financial, HR) under separate identity providers.
2. Endpoint and server protection
- Apply application allowlisting or other execution controls to prevent unauthorized code.
- Keep all OS and application patches current, including VPNs and remote-access software.
- Disable unused services (FTP, RDP, SMBv1) to shrink the attack surface.
- Monitor for unsigned or sideloaded executables, especially in document workflows.
3. Email and phishing defense
- Deploy anti-phishing and sandboxing for attachments and links.
- Tag external emails and train staff to recognize credential-harvest attempts.
- Implement DMARC, SPF, and DKIM to authenticate outgoing messages.
4. Network segmentation and continuous monitoring
- Separate academic research, student, and corporate networks.
- Restrict east-west traffic between network zones.
- Deploy network detection and response (NDR) tools to identify lateral movement.
- Correlate DNS, proxy, and authentication logs within a centralized SIEM.
5. Data governance and encryption
- Encrypt sensitive data at rest and in transit, including internal email stores.
- Apply role-based access controls to donor and student data.
- Deploy data loss prevention (DLP) to stop exfiltration via cloud or removable media.
6. Incident response and resilience
- Maintain offline, immutable backups of critical databases.
- Conduct quarterly tabletop exercises simulating credential theft and ransomware.
- Document and test escalation paths to legal and communications teams.
ThreatLocker Zero Trust protections for universities
1. Application control
- Enforce default-deny Application Allowlisting across faculty and administrative endpoints.
- Approve only known, signed applications such as document editors, browsers, and teaching software.
- Use Learning Mode briefly, then switch to enforcement to lock in a clean baseline.
2. Ringfencing
- Block allowed applications from launching PowerShell, Command Prompt, or accessing network drives unless explicitly required.
- Deny inter-process communication between Office apps and browsers to stop macro-based credential theft.
- Restrict outbound network access for critical applications to allowlisted domains.
3. Storage control
- Prevent use of unauthorized USB drives or external media.
- Allow only encrypted, company-issued devices with audit logging enabled.
- Limit write permissions on departmental shares containing student or donor information.
4. Network and privilege integration
- Combine with MFA and privileged-access management (PAM) solutions.
- Use Elevation Control for just-in-time approval of privileged actions.
5. Monitoring and response
- Enable Audit Mode to review new or blocked applications and flag anomalies.
- Integrate ThreatLocker logs with a SIEM for real-time alerts.
Frequently asked questions
What caused the University of Pennsylvania data breach?
Attackers allegedly gained access through a compromised PennKey login, moving laterally into multiple internal systems.
What information was exposed in the Penn breach?
The incident reportedly exposed student, donor, alumni, and employee records, including financial and contact details.
How did the attackers use the compromised accounts?
They sent mass emails mocking the university and threatening to leak data, escalating the reputational impact.
Why are universities frequent targets of cyberattacks?
Academic institutions hold valuable research, donor networks, and student data, often on loosely federated systems.
How does ThreatLocker help protect higher education networks?
The ThreatLocker Zero Trust platform blocks unauthorized software, isolates applications, restricts network access, and enforces least privilege to stop lateral movement and data theft.





