Ransomware is malicious software that encrypts files, locking a victim out of their confidential data. If the victim pays the ransom, they may receive a decryption key that will restore their files and data access. If the demanded ransom is not paid, the threat actor may leak their data-on-data leak sites (DLS) such as the dark web and/or permanently block access to their files. As ransomware is distributed by cybercriminals, there is no guarantee that files will be decrypted if the ransom is paid, or that data wasn’t immediately leaked onto the dark web.
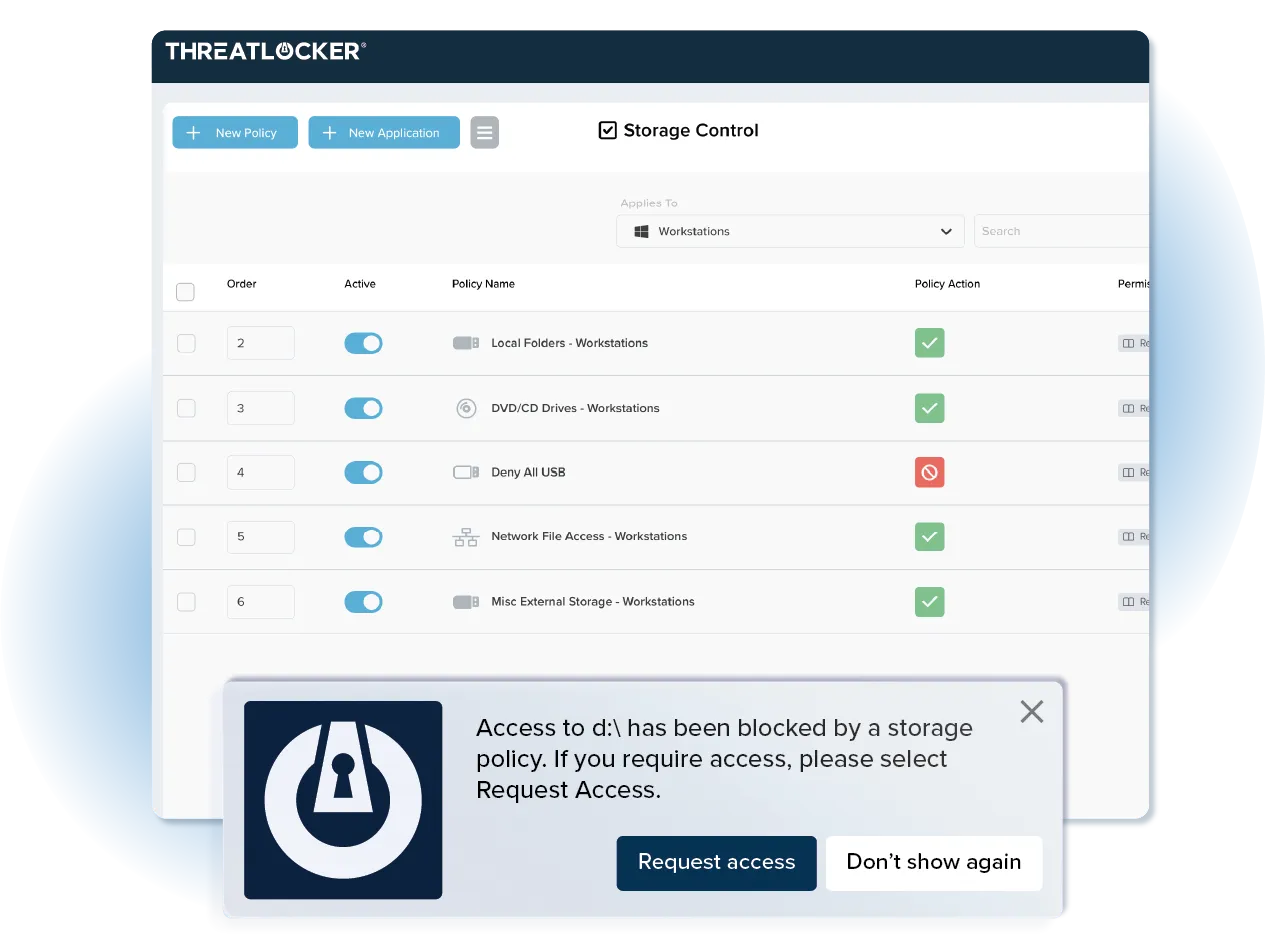
Application Allowlisting denies all executables, libraries, and scripts from executing, except those that are explicitly permitted to run in an environment.
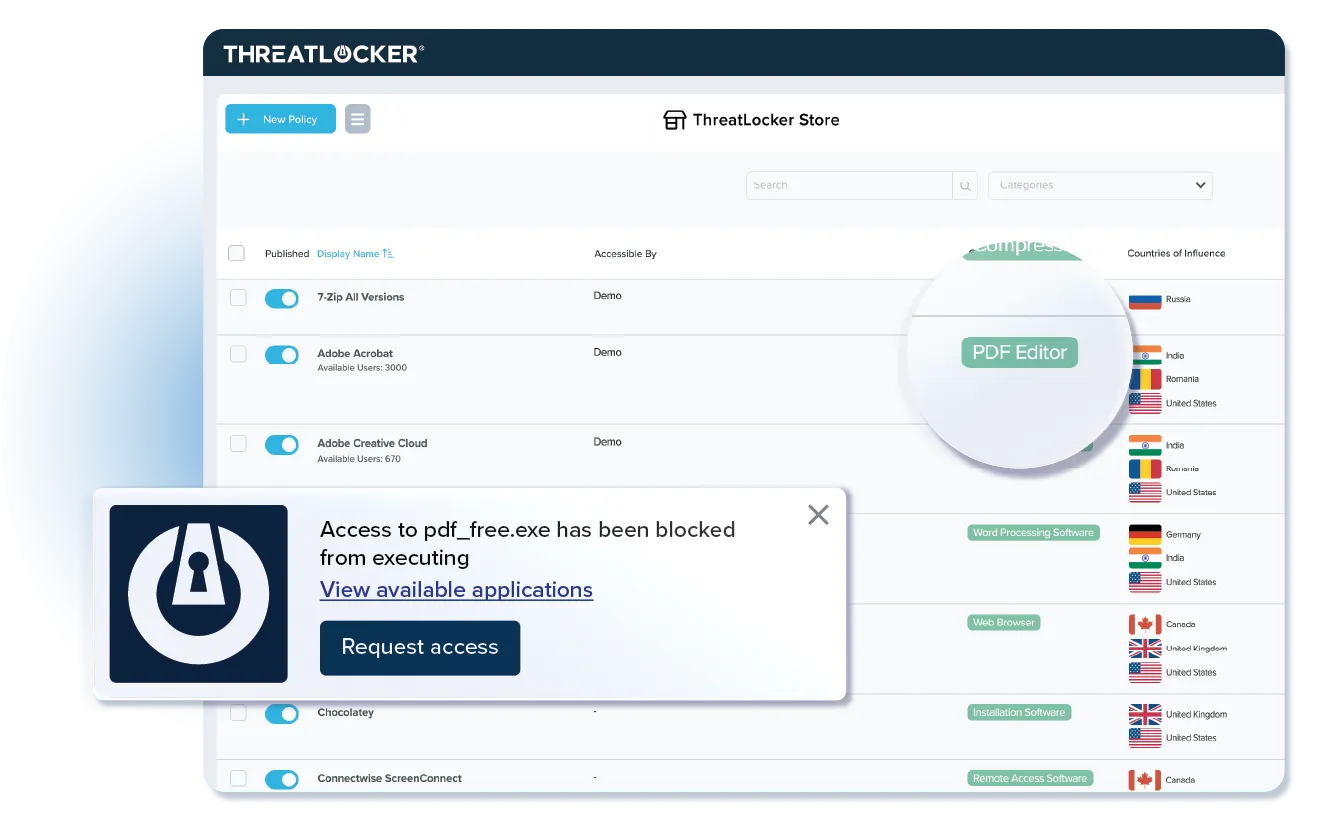
Many cybercriminals use legitimate encryption tools such as 7-Zip to encrypt files. By using Allowlisting, legitimate tools that have not been explicitly allowed, including those that could be used to encrypt data, are blocked.
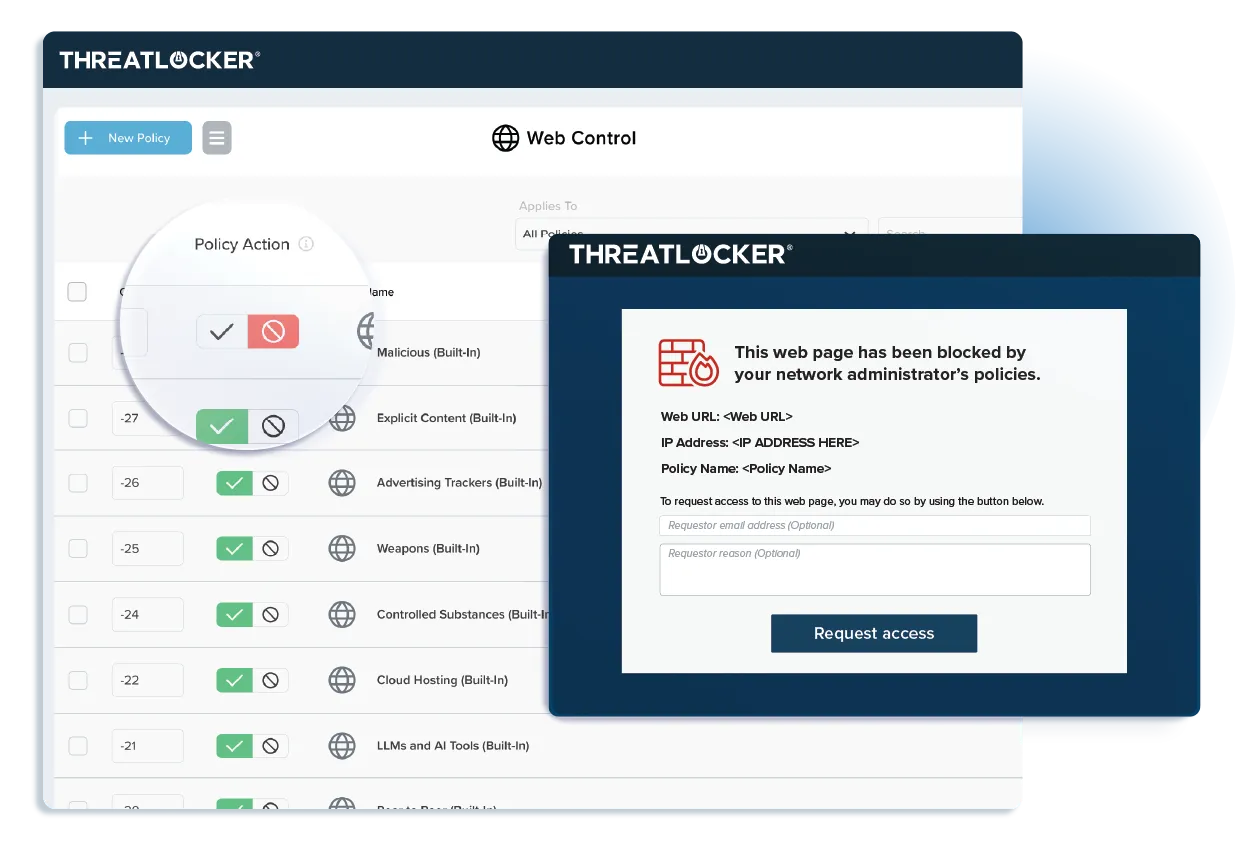
The process of deploying Allowlisting is extremely simple. ThreatLocker learns what is required in your environment and, once secured, blocks everything else.

Try ThreatLocker free for 30 days and experience full Zero Trust protection in your own environment.
Schedule a customized demo and explore how ThreatLocker aligns with your security goals.
Just starting to explore our platform? Find out what ThreatLocker is, how it works, and how it’s different.