Table of contents
As a new ThreatLocker user, you might initially feel overwhelmed by the interface. However, the setup process is designed to be straightforward. Here's a simple list of things to do when you first join.
ThreatLocker User Page
The first page you should focus on is the User Page. You can create new users and assign them specific roles and permissions. Multiple roles are crucial to ensure the right level of access and control. For instance, you might not want admins to change billing information or other admins' permissions.
ThreatLocker Computer Page
After setting up your User Page, the next step is to focus on the computer tab. Here, you'll create computer groups, which are crucial for organizing and managing different types of computers with specific needs, just like you did for the User Page.
Here are some examples of groups that you might want to have:
- IOT (Internet of Things) - IOT computers, like computers, are used for TVs or kiosks.
- Front Desk - For the front desk computer.
- HR - For the HR department.
- DEV - For the development department.
Each of these groups will have very different needs. The IOT computer might never need access to PowerShell or a web browser. However, a development computer would use other tools like PowerShell and run unsigned versions of the software they are developing or testing.
Now that your computer groups are set, you can begin installing ThreatLocker. On initial installation, your machine will be put into baseline mode, which will put it into a baseline state and learning mode (it will take two weeks to learn what software is being used).
ThreatLocker Application Control Page
The Application Control page holds all the software that is allowed or denied. This page also allows you to make any software policy. If you don't see any policy at the "entire organization level," that policy might be on a different hierarchy level.
The organization hierarchy level goes by the following:
- Entire organization level
- Individual computers
- Computer groups
Note:
- Policies are applied top-down, so if you have a policy at the Entire Organization level, it will take priority over the computer group and individual computer policies.
- If no policy covers a particular software, it will automatically block it from running.
Here are some examples of when you would use each level for a policy.
- Entire organization level - Deny video game launches for the whole organization .
- Individual computers - Allow computer drivers for a particular computer.
- Computer Groups - Allow HR software only in the HR group.
What type of policy should be made?
The most common policies are for new software that the company has started to use. Another is explicitly denying software like Video game launchers.
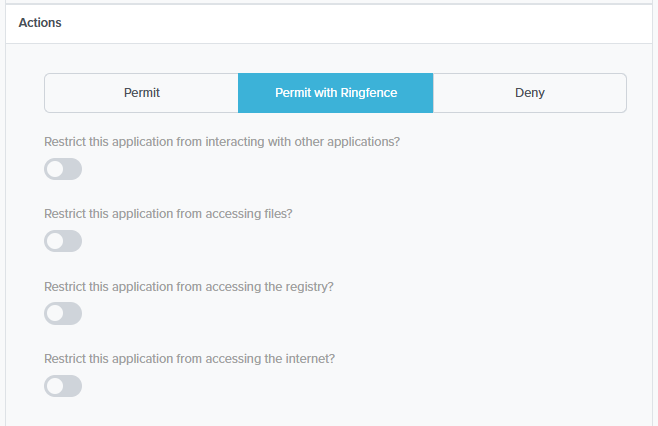
What is Ringfencing™?
Ringfencing™ is another step to locking down your computers. It allows you to block software from connecting to the internet, making registry changes, accessing files, and interacting with other applications.
Why should people use Ringfencing™?
The most common problem with allow-listing software is what if the allowed program is now doing malicious things, like making an internet connection to a server that the program has never done before.
Example of some Ringfencing™ policies
- Block Web browsers from interacting with the terminal.
- Blocking office software from accessing the internet except for the update servers.
ThreatLocker® Resources
ThreatLocker® offers free resources to all organizations, whether they are clients or not. To learn more about how the Zero Trust Endpoint Protection Platform, visit:
- Resource Center | ThreatLocker, Inc.
- Home | ThreatLocker Help Center (kb.help)
- Try ThreatLocker Endpoint Protection Platform Free
Take Control of Your Cybersecurity with a Free Trial from ThreatLocker






