Table of contents
What is the Pool Party Exploitation technique?
This technique allows a hacker to inject malicious code into an existing process. After doing this, the hacker has complete control over the target machine. This type of exploit has been detectable by EDR vendors for years. However, SafeBreach, the creators of the exploit, has stated that the Pool Party technique goes completely undetected by five of the leading EDR solutions.
What is vulnerable, and how bad is it?
ALL versions of Windows are currently vulnerable. If you are only relying on EDR to protect your systems, then this is a CRITICAL vulnerability.
Recommendations for everyone
EDR vendors are currently working on an update to address this issue. Monitor your EDR vendor for further instructions.
Recommendations for ThreatLocker customers
This attack requires the execution of a malicious process. This will be automatically stopped by ThreatLocker Application Whitelisting.
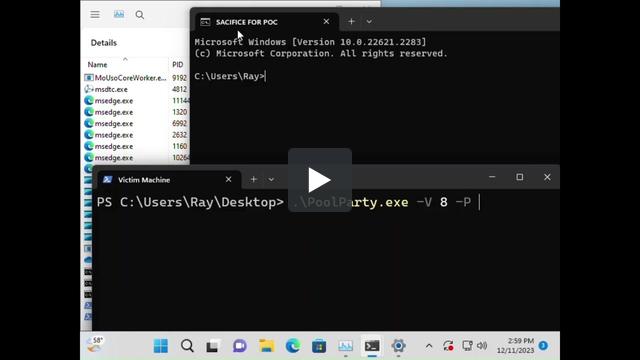
Video demonstration of Pool Party Exploit
Video timestamps
0:00:04 - Find a sacrificial process for Pool Party to inject malware into. In our case, a cmd.exe process.
0:00:05 - Go to task manager to get the PID of the sacrificial process (cmd.exe).
0:00:10 - Run the exploit which injects our malicious shell code into the sacrificial process (cmd.exe).
0:00:12 - The sacrificial process dies and spawns a thread containing our malicious shell code.
0:00:23 - From the Attacking machine you can see that the victim has called home and given the attacker complete control.
0:00:28 - To prove complete control the attacker can send any commands they want to the victim. In this case, the attacker spawned a dancing parrot.