ThreatLocker® Defense Against Configurations (DAC) Dashboard
See how DAC automatically identifies misconfigurations and maps them to your environment’s compliance and security requirements
Why your environment needs DAC
You can prevent many cyberattacks by simply eliminating your misconfigurations.
An unused admin account left active. A firewall rule no one remembers adding. A default Windows setting that quietly weakens your defenses.
These small gaps often go unnoticed, but they’re exactly what attackers exploit to gain a foothold.
What is DAC?
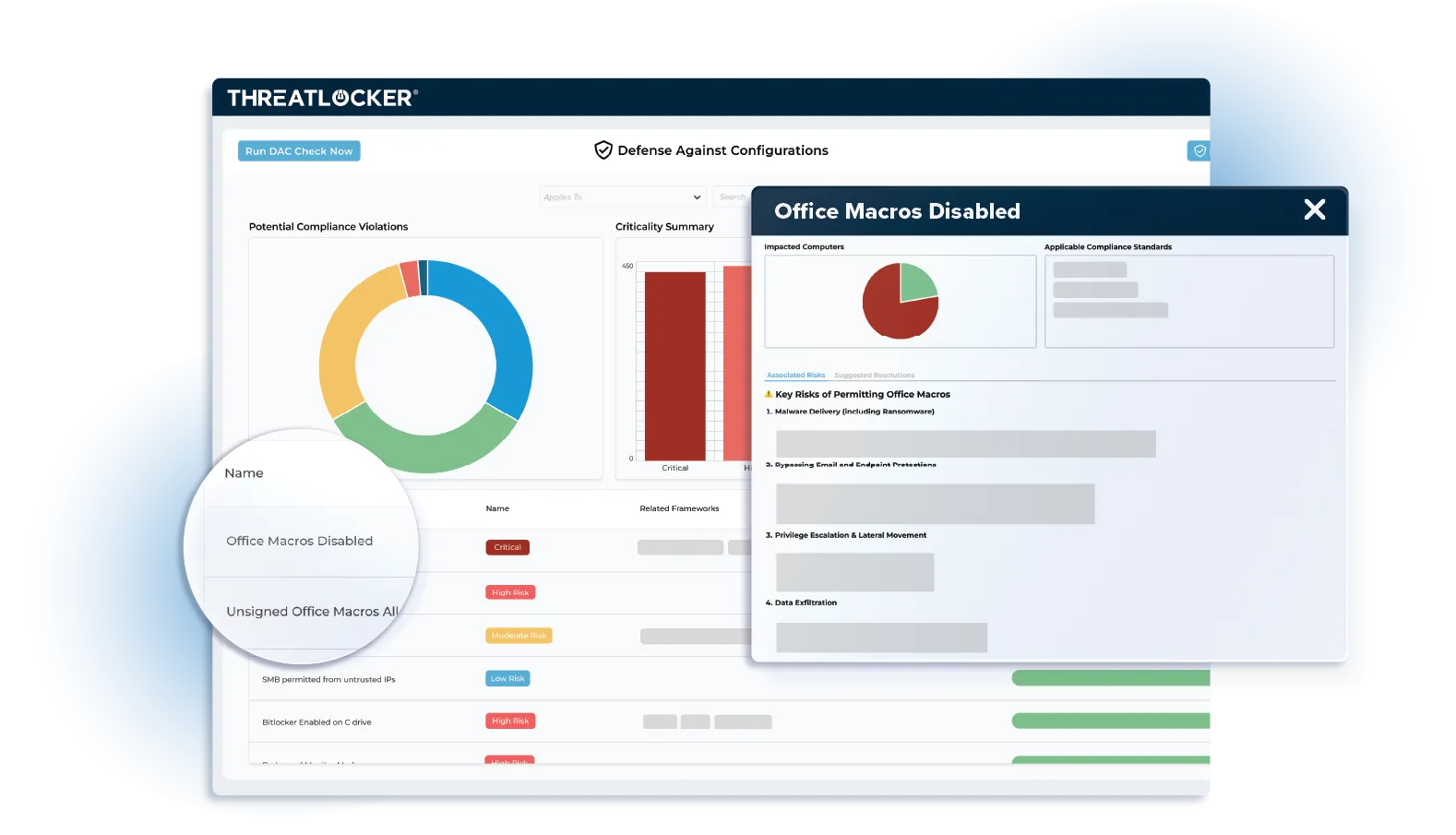
ThreatLocker DAC is a powerful dashboard, built right into the ThreatLocker agent. It shows you exactly how your systems are configured and what needs fixing. Think of it as your ultimate resilience assessment center.
DAC allows security teams to:
- Identify misconfigurations before they become exploited vulnerabilities
- Highlight current USB drive permissions
- Monitor configuration compliance with major frameworks
- Receive clear, actionable remediation guidance
- Understand risk levels across all endpoints in one place
DAC removes the guesswork by flagging risky settings, highlighting dormant admin rights, and mapping gaps against compliance standards.
How DAC works
Once enabled, DAC becomes the default landing page in your ThreatLocker portal. The dashboard provides a daily scan of your systems, delivering a unified view of configuration issues sorted by severity. Visual summaries and sortable lists make it easy to filter by endpoint, compliance framework, or risk level.
DAC is lightweight and operates directly on the endpoint. It captures configuration data at the source without adding performance overhead. Because DAC lives inside the ThreatLocker platform, there is no need for additional software, integrations, or licensing.
Each week, administrators receive an email showing the number of critical configuration issues. The summary includes color-coded severity boxes, a list of affected systems or policies, and suggested remediations.
Get the DAC one-pager
Download the one-page overview to learn how DAC surfaces risky settings, prioritizes what to fix, and helps you tighten security fast.
Key benefits of ThreatLocker DAC
Real-time visibility
See your organization’s configuration posture clearly and act quickly on misconfigurations.
Improved security
Address the root causes of many breaches by eliminating common but dangerous system setup flaws.
Simplified compliance
DAC aligns your configurations with standards such as NIST, Essential 8, CIS, HIPAA and ISO 27001.
Actionable insights
Get step-by-step guidance on how to correct each issue and close compliance gaps faster.
Unified experience
Access all findings in a single, filterable dashboard without needing multiple tools or reports.
FedRAMP support
DAC flags NIST 800-171 and NIST 800-53 control gaps so you can fix issues, pass audits, and stay secure.
start Your path to stronger defenses
Get a trial
Try ThreatLocker free for 30 days and experience full Zero Trust protection in your own environment.
Book a demo
Schedule a customized demo and explore how ThreatLocker aligns with your security goals.
Ask an expert
Just starting to explore our platform? Find out what ThreatLocker is, how it works, and how it’s different.