Table of Contents
Organizations utilizing the ThreatLocker® Zero Trust Endpoint Protection Platform have an advantage over threat actors. With robust controls and monitoring capabilities, ThreatLocker® mitigates the threat of data breaches and malicious software in an environment.
ThreatLocker® provides cybersecurity reports to clients and partners to understand what is occurring within their environment. Below are five of the top reports in which clients can utilize.
How To Run ThreatLocker® Reports
Once you have logged in to the ThreatLocker® Portal, follow the below steps:
- Navigate to the Menu Bar.
- Select the "Reports" tab.
- Select the Report you need in the dropdown.
- Select the "Generate" button.
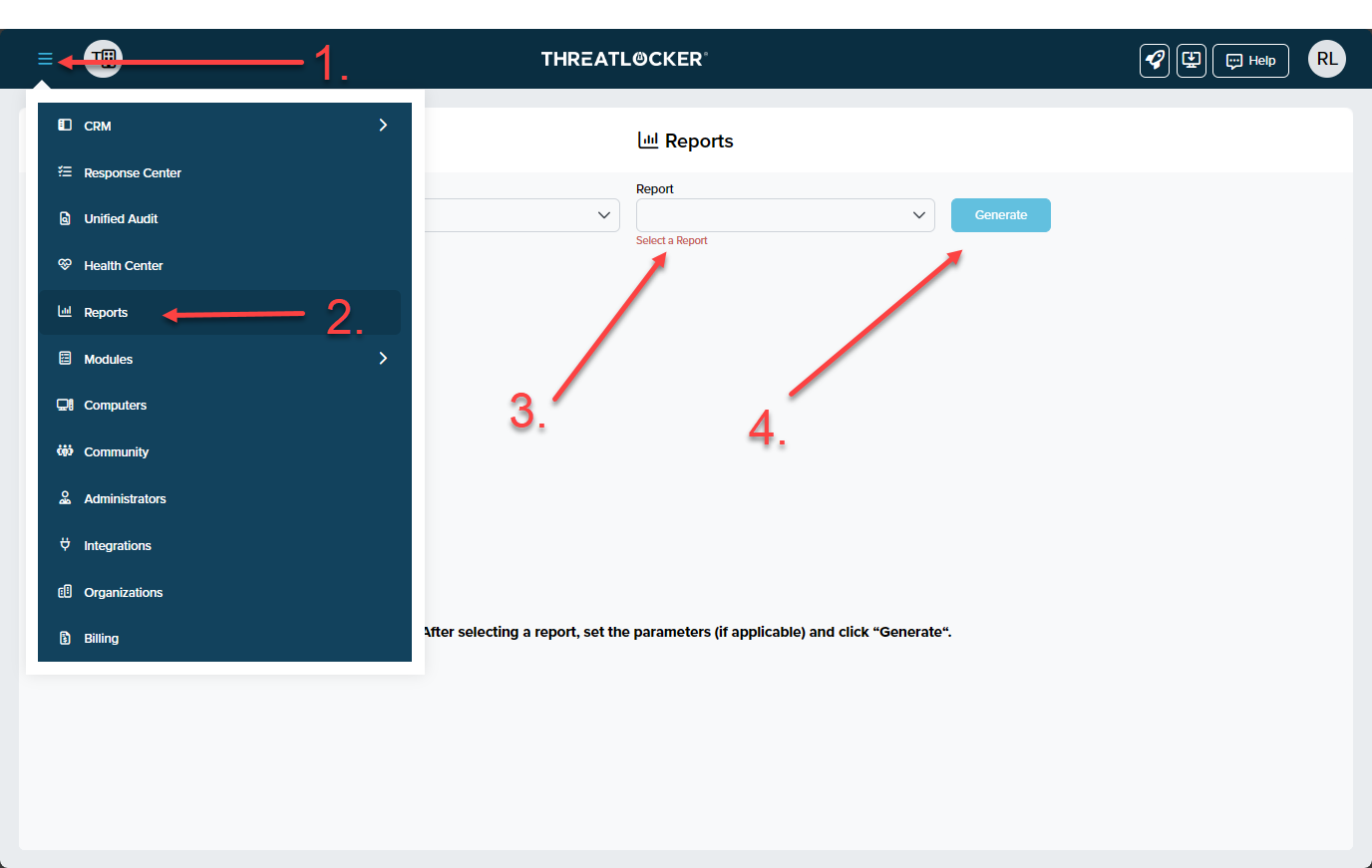
ThreatLocker® Report #5: "Non-Encrypted USB Devices" and "USB Activity in the Last 7 Days"
These reports enable you to view the USB devices that have connected to endpoints in your environment within the past week. Understanding USB usage enables you to make informed decisions when creating Storage Control policies.
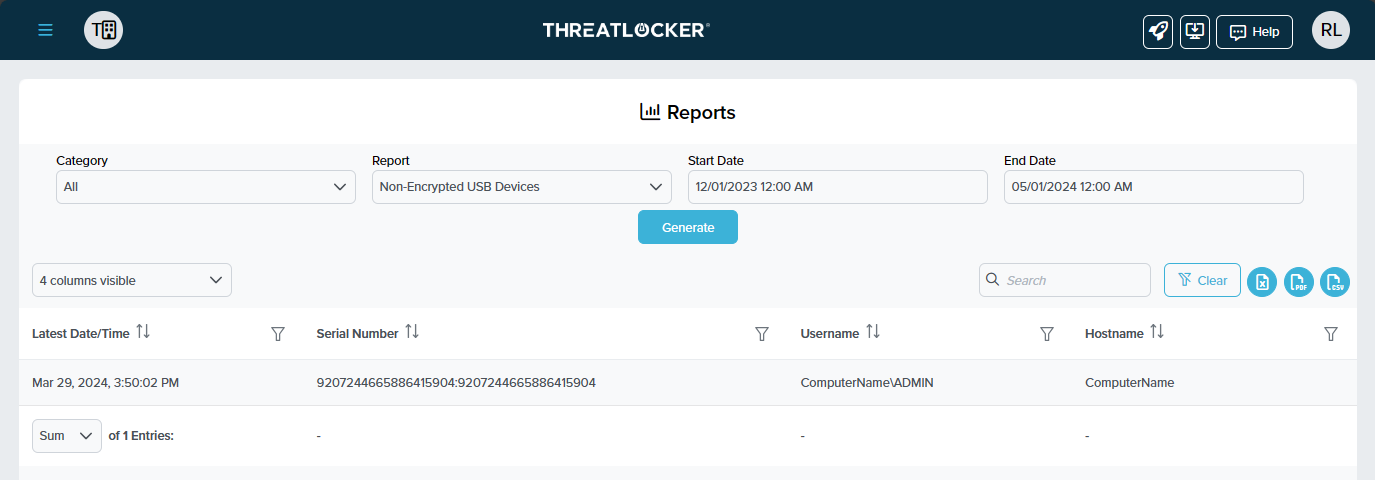
ThreatLocker® Report #4: "Local Admin Elevated Programs in the Last 7 Days"
This report actively records programs executed with administrator-level access, detailing the involved user and computer. Refining Ringfencing™ or ThreatLocker® Detect policies is essential to ensure that only authorized programs run with elevated privileges.
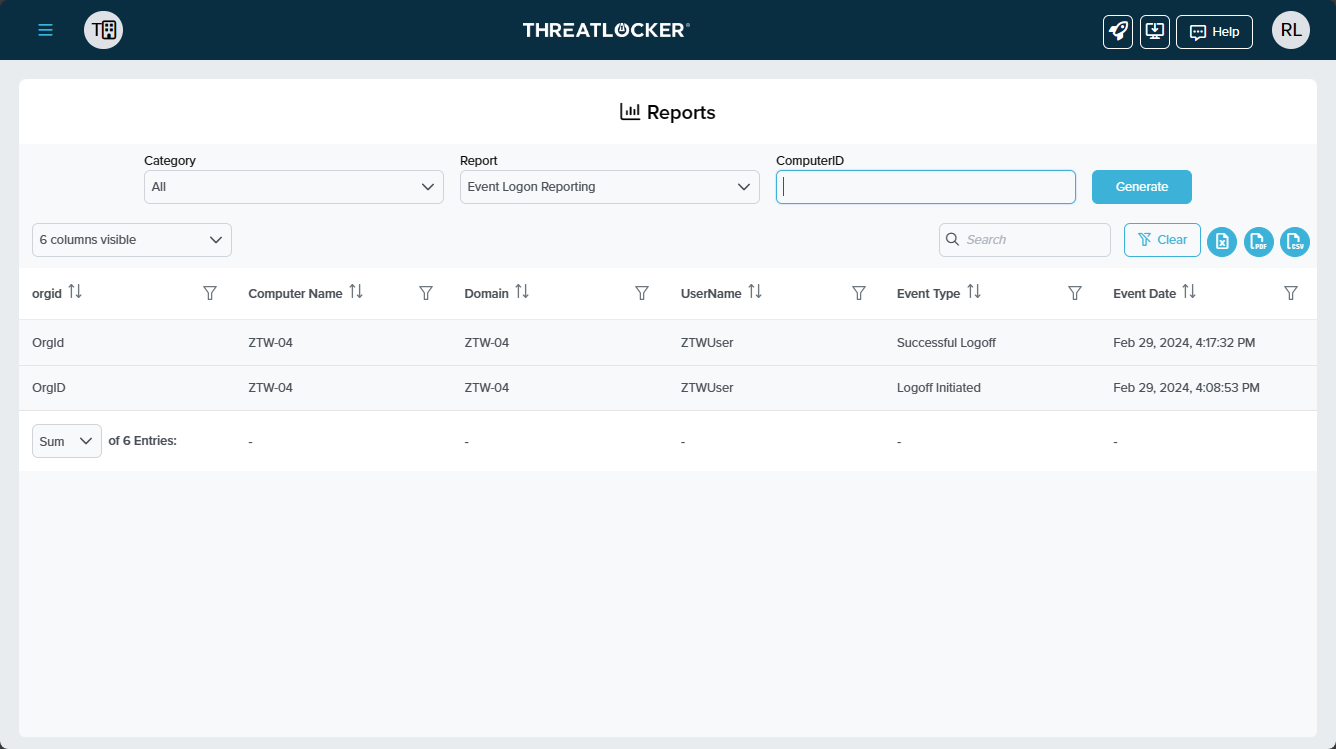
ThreatLocker® Report #3: "Event Logon Report"
The Event Logon Report uses computer IDs to detail who has logged onto which machines. This report is beneficial for monitoring computers that have infrequent logins.
Note: This report only includes data retained according to the ThreatLocker® retention policy.
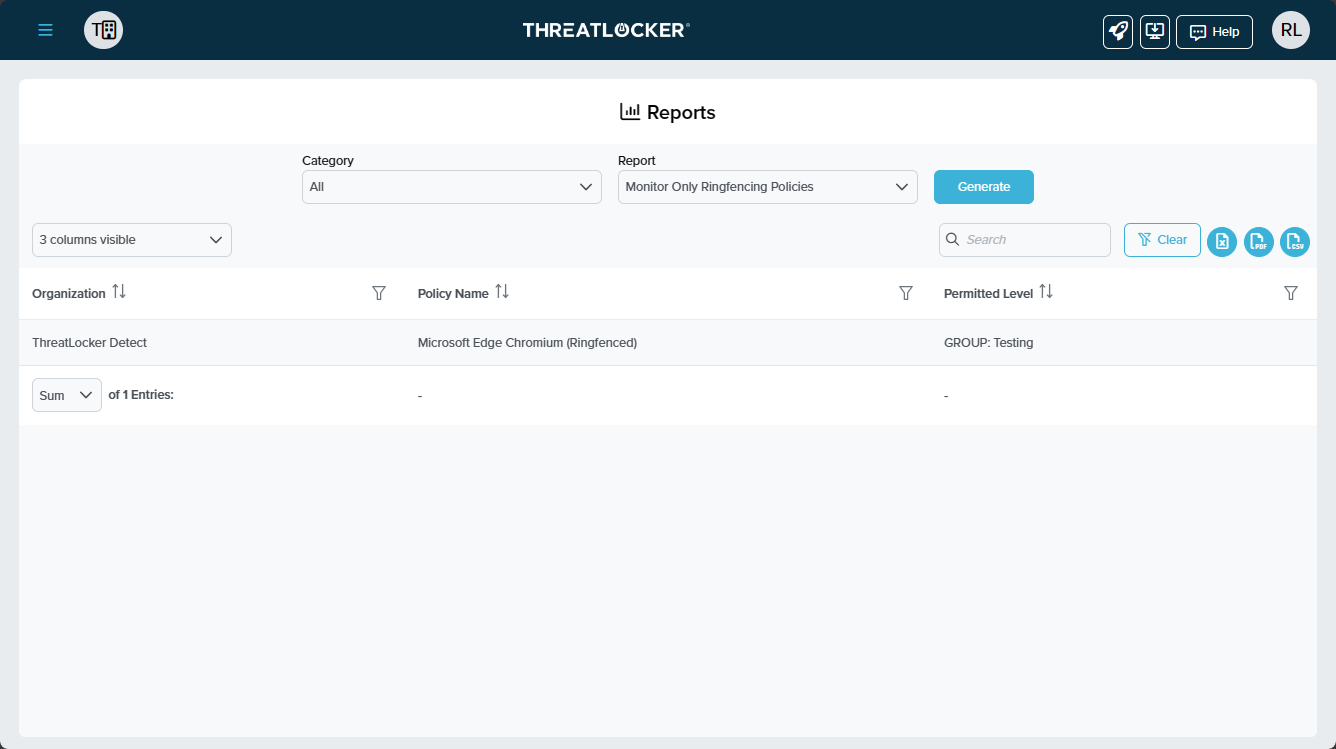
ThreatLocker® Report #2: "Monitor Only Ringfencing™ Policies"
This report identifies Ringfencing™ policies currently set to "monitor only," indicating that they do not actively intervene when triggered. Reviewing this can help determine if changes are necessary to move from monitoring to active enforcement.
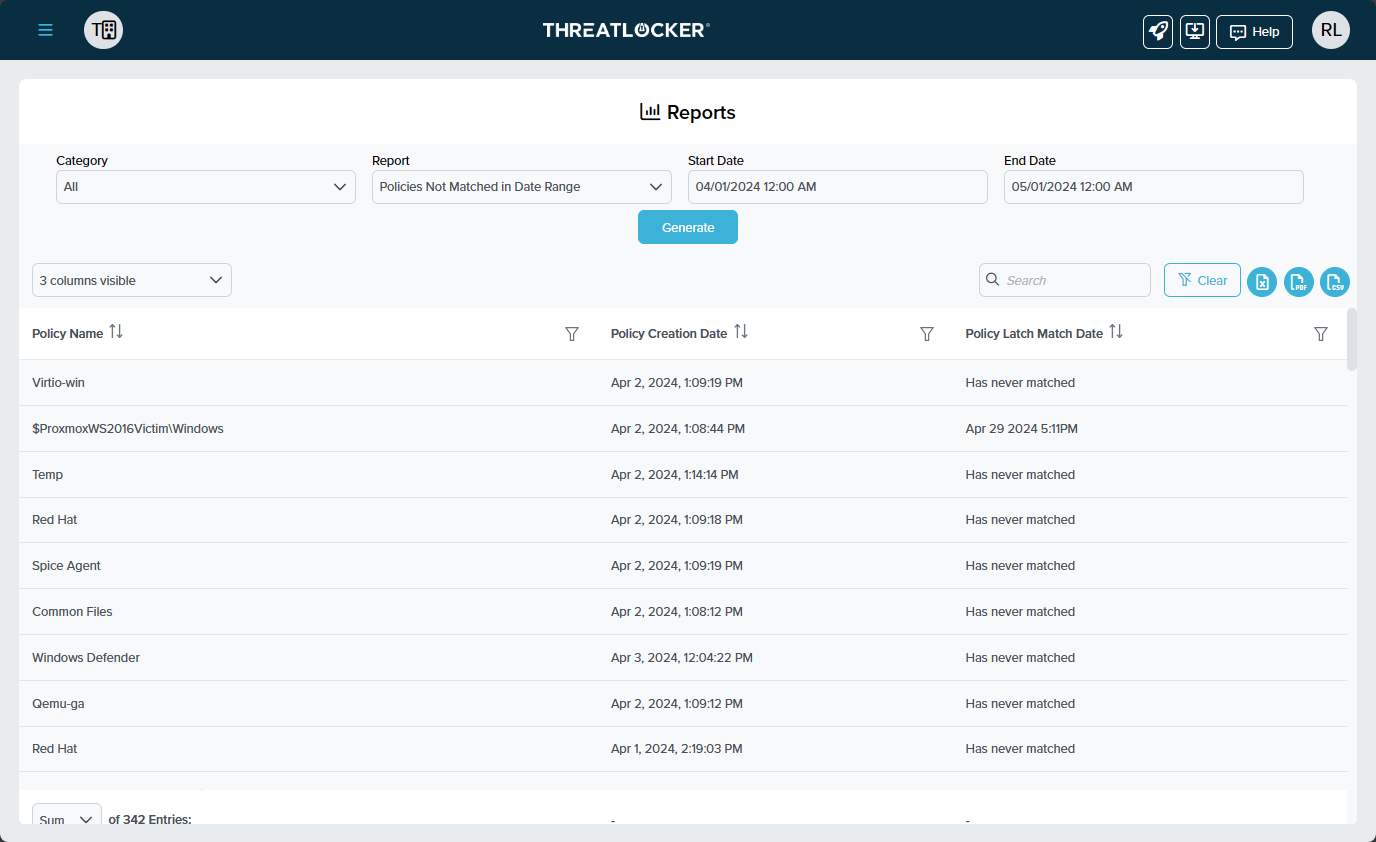
ThreatLocker® Report #1: "Policies Not Matched in 180 Days" & "Policies Not Matched in Date Range"
These critical reports identify policies not triggered within the specified timeframe. This information is crucial for administrators to streamline and update the policy list, removing obsolete or unneeded entries.
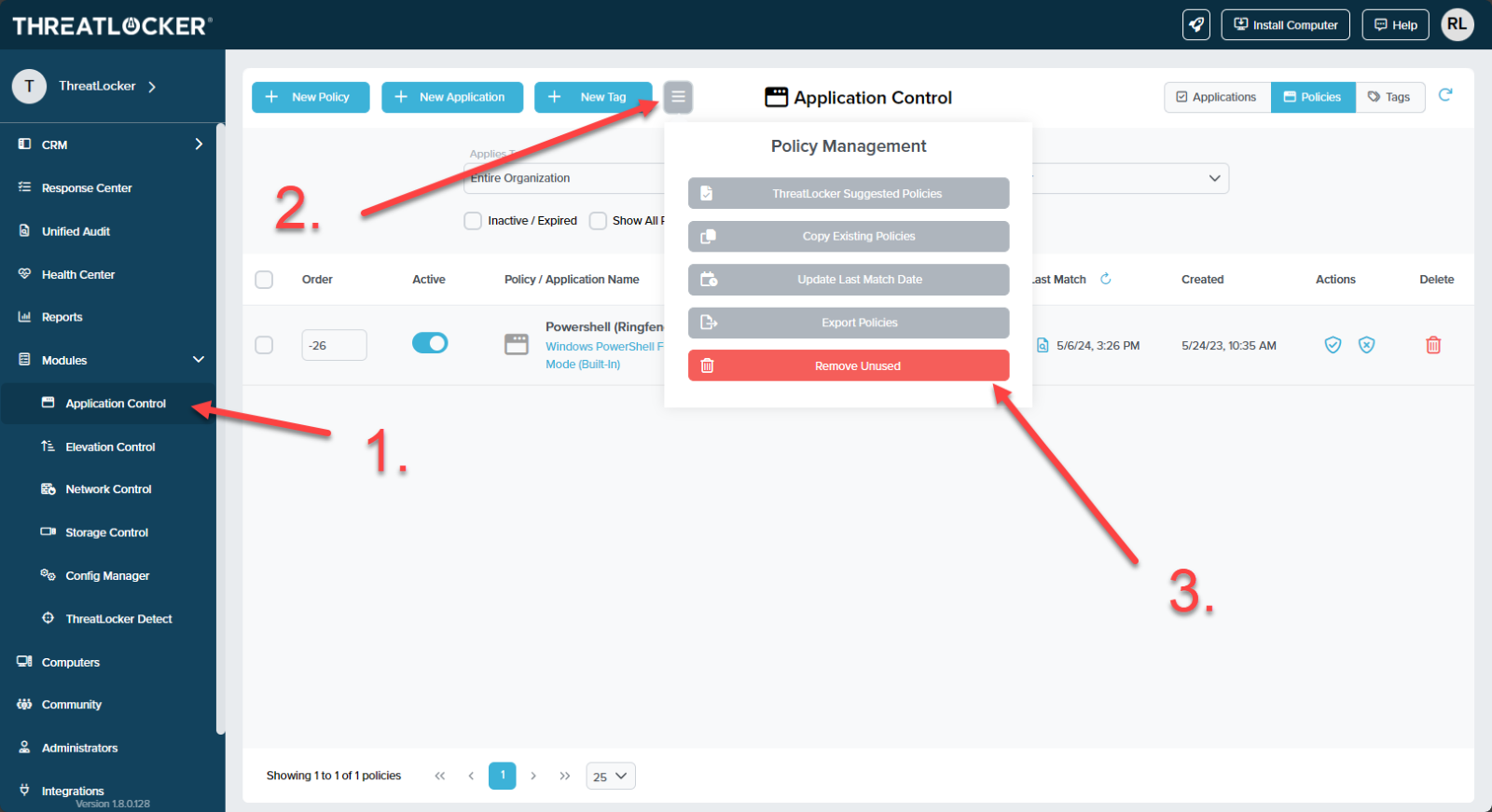
Users can also use a button in both applications and policies page under the "Application Control" module, where it will remove unused software and policies
Bonus Reports!
ThreatLocker® Report #6: "All Hostnames and Usernames"
This report provides IT professionals with crucial insights for managing user access and tracking device usage. It does this by listing all hostnames and usernames within the environment.
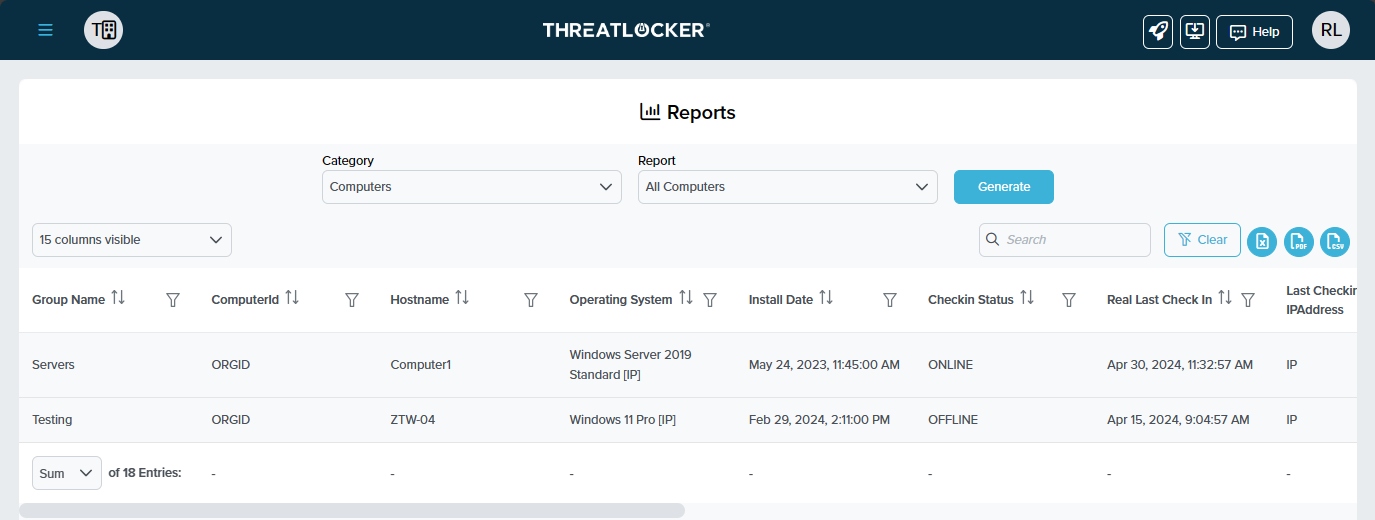
ThreatLocker® Report #7: "All Computers"
The "All Computers" report includes Group ID, Computer ID, and operating system details for each computer in your network. This is invaluable for inventory management and ensuring that all systems are up-to-date and secure.
ThreatLocker® Resources
ThreatLocker® offers free resources to all organizations, whether they are clients or not. To learn more about how the Zero Trust Endpoint Protection Platform, visit:
If you are not a client but would like to take the steps to implement ThreatLocker® into your cybersecurity strategy, you can sign up for a free trial or book a demo with a ThreatLocker® Cyber Hero.