-with-MacOS-Blog-Header-Photo.webp)
How Hackers Use Bluetooth to Take Over Your Mac Device
Table of Contents
Summary
What if I told you someone could take control of a device without any physical interaction with it? What if I told you they can mask themselves as your favorite Bluetooth Headset or keyboard? This is the power Bad Bluetooth or Bad KB Attacks have. In this article, we will cover how hackers can leverage your Bluetooth devices to gain a foothold on your device and how to mitigate these attacks.
We recently conducted a webinar featuring Danny Jenkins, CEO of ThreatLocker, Rob Allen, CPO of ThreatLocker, and Cybersecurity Engineer Ivan Fonseca. During the webinar, they demonstrated the Bluetooth impersonation vulnerability in Mac devices and discussed effective mitigation strategies. To learn more about this vulnerability and how to protect your Mac devices, watch the webinar recording to see how it's done.
About Bluetooth
Bluetooth is a wireless communication protocol that facilitates seamless connectivity between electronic devices. As a digital intermediary, Bluetooth enables gadgets like smartphones and headphones to establish communication without needing physical connections. Essentially, devices labeled as "Bluetooth-enabled" have the capability to engage in wireless dialogue akin to a proprietary language exclusive to them. This technology is the conduit through which devices exchange information, enabling functionalities such as wirelessly streaming music from a smartphone to headphones or facilitating communication between a keyboard and a computer, eliminating the constraints imposed by physical cables.
What is a Bluetooth Impersonation Attack (BIAS)?
A Bluetooth Impersonation Attack (BIAS) is a type of cyberattack where hackers exploit vulnerabilities in the Bluetooth communication protocol to impersonate trusted devices and gain unauthorized access to target Bluetooth-enabled devices. So, technically, it's the hacker playing with the first steps of the connection, tricking the devices into thinking they're dealing with a trusted friend. This technique grants hackers unauthorized access to the targeted systems. BIAS is slick because it occurs during the initial Bluetooth connection, making it a real challenge to spot.
How Hackers Exploit Bluetooth
Hackers can exploit Bluetooth vulnerabilities, leveraging tools such as Flipper Zero, Bad KB Attacks, and Bluetooth spoofing techniques. Flipper Zero, a versatile hacking device, can manipulate Bluetooth connections maliciously; we will break down the latest tools hackers use to control your endpoint.
Flipper Zero
Bad KB/Bad BT
- Bad KB allows an attacker to send keystrokes to a device that has paired with it. Essentially acting as a Rubber Ducky with Wireless Capabilities.
Marauder
- Marauder is a tool for the Flipper Zero with both Wi-Fi and Bluetooth sniffing capabilities. This tool lets an attacker sniff all devices in the area. Allowing them to retrieve important data such as Bluetooth Device name and MAC Address. It is important to note that an ESP32 Dev Board is necessary for this to work with the Flipper Zero.
Kali Linux
Hcitool
- Much Like Marauder, Hcitool is a Bluetooth reconnaissance tool that allows you to sniff all Bluetooth Devices in the area with a simple Bluetooth card or Bluetooth adapter.
Attack in Action
In our presentation, we'll demonstrate a direct approach to compromising MAC OS machines. We'll kick things off using hcitool to extract MAC addresses from trusted devices. Following that, we'll discuss how attackers can manipulate this data to trick MAC OS machines into thinking an imposter device is trustworthy.
The pivotal moment in our demonstration involves the strategic use of Flipper Zero, a versatile hacking tool. With Flipper Zero, we'll initiate a BAD KB payload, allowing attackers to remotely manipulate the MAC OS machine by sending keystrokes. This demonstration underscores the need for heightened awareness and robust defenses against potential security breaches in the context of MAC OS systems.
Phase 1 - Enumeration
We'll rely on a Kali Linux package called BlueZ to execute this phase. BlueZ facilitates the utilization of the hcitool tool, enabling us to carry out Bluetooth device sniffing effectively.
- Ensure you have a Bluetooth adapter to sniff devices in your proximity:
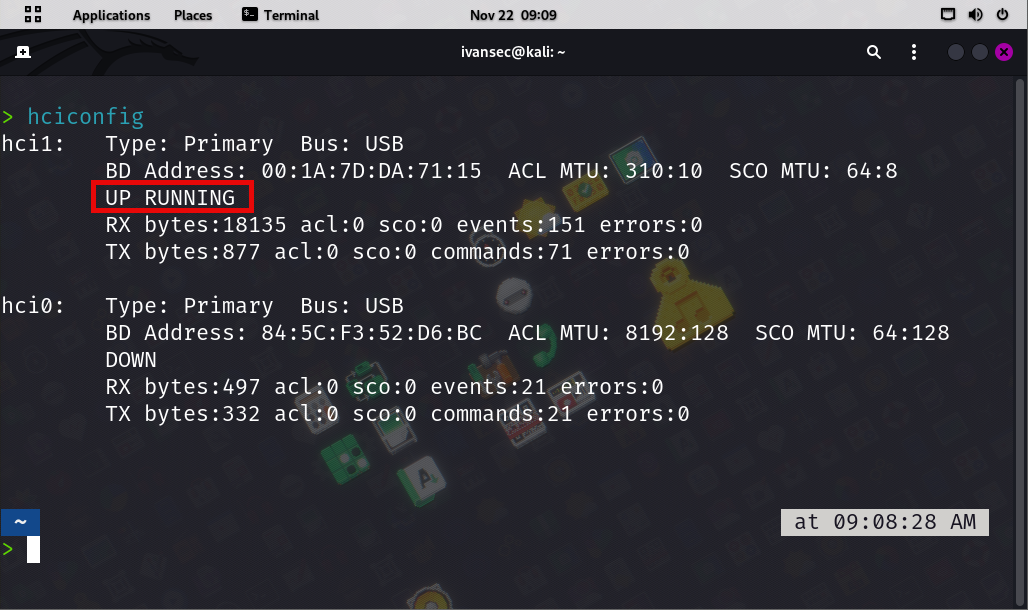
- If your adapter is currently "DOWN" set it to an "UP" state by:

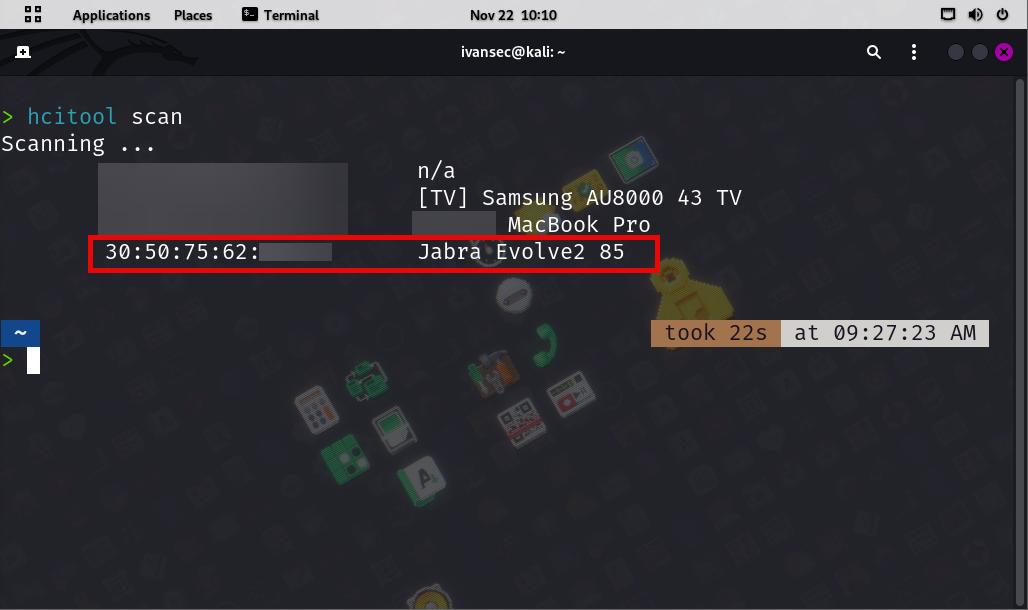
- Finally we start listening for Bluetooth devices, for this example we will impersonate Jabra Evolve2 85:
Phase 2 - Exploitation
In this phase, you'll need a Flipper Zero with either the Bad KB or Bad BT Module. Although it's not strictly necessary to use Unleashed Firmware, we have opted to utilize the Unleashed Firmware package for this specific test.
Attackers POV
Video Breakdown:
00:07 - Open Bad KB/Bad BT Module on your Flipper
00:13 - Select Payload of Choice
00:18 - Select and Configure BT Device Name
00:55 - Select and Configure BT MAC Address
01:19 - Wait for the victim to Connect
01:21 - Run Payload
Victims POV
Video Breakdown:
00:07 - Victim Opens Bluetooth Settings
00:12 - Victim Imitates the pairing process with a trusted device
00:19 - Flipper intercepts connection due to MAC Address Spoofing
00:20 - Keystroke Injection sent from Bad KB/BT
00:27 - Reverse Shell Connection Requested via Terminal from Victim Machine
00:29 - Successful Rick Roll
Mitigation
Connecting Bluetooth devices requires caution. Make sure you're connecting to your actual device. Some attackers might not go all the way to spoof your MAC address, but they could deploy multiple Bluetooth devices with a name similar to yours. Stay vigilant. Our team at ThreatLocker has made it our utmost priority to ensure your security. With Ringfencing™ for Mac Endpoints, we stopped the ongoing exploitation of this attack. Simply put, the ThreatLocker Ringfencing™ solution proactively prevents applications from communicating with each other, your files, or the internet. In a basic sense, if attackers attempted a reverse shell connection through a trusted app like Terminal, Ringfencing™ would efficiently thwart this action by recognizing Terminal's attempt to access the internet. It adds a layer of security to prevent unauthorized actions.



